If you hold digital assets, you’ve likely heard the terms multi-signature wallets and smart contract wallets. Both aim to protect funds and coordinate control, but they solve the problem differently. In short: a multi-signature (multisig) wallet requires M-of-N independent keys to approve a spend, while a smart contract wallet (SCW) is an on-chain program that enforces rules—signers, limits, recovery, and more—before moving funds. This guide explains the differences so you can pick the right setup for individuals, teams, and DAOs. This content is educational, not financial or security advice—consult qualified professionals before deploying high-value custody.
Quick answer: choose a multisig when you need simple, durable shared control with independent keys; choose a smart contract wallet when you want programmable policies (limits, timelocks, social recovery, gas abstraction) and are comfortable with contract risk.
Fast path to action: define your risk, pick the model (multisig or SCW), set signer/policy counts, test small, monitor activity, and formalize incident response.
1. Custody Model: Keys-as-Checks vs Code-as-Policy
A multi-signature wallet enforces security by requiring multiple independent private keys to co-sign a transaction; the transaction is valid only when at least M out of N signatures are present. This creates resilience: one lost or compromised key does not unilaterally move funds. In contrast, a smart contract wallet enforces security through on-chain code that defines who can act and under what conditions (e.g., daily limits, whitelists, delays). You still sign, but the contract decides whether to honor that action based on its rules. In practice, multisig leans on cryptography and threshold approval, while SCW leans on programmability and verifiable logic. Both approaches are widely used: multisig is foundational in Bitcoin and Ethereum treasuries; SCWs have risen with account abstraction and contract standards.
Why it matters
- Failure isolation: Multisig isolates key failure; SCW isolates policy failure (bugs) with audits and upgradability choices.
- Complexity surface: Multisig is conceptually simple; SCW can encode rich but more complex rules.
- Transparency: Multisig conditions are implicit in signatures; SCW rules are explicit in code.
Numbers & guardrails
- Typical team treasuries use 2-of-3 or 3-of-5 multisig; larger DAOs often use M-of-7 to M-of-15.
- For SCW policies, many teams mirror a 3-of-5 approval but add a 24–72 hour timelock on high-risk actions.
Bottom line: choose multisig for minimal moving parts and distributed trust; choose SCW when you need expressive, reviewable policy that can evolve over time.
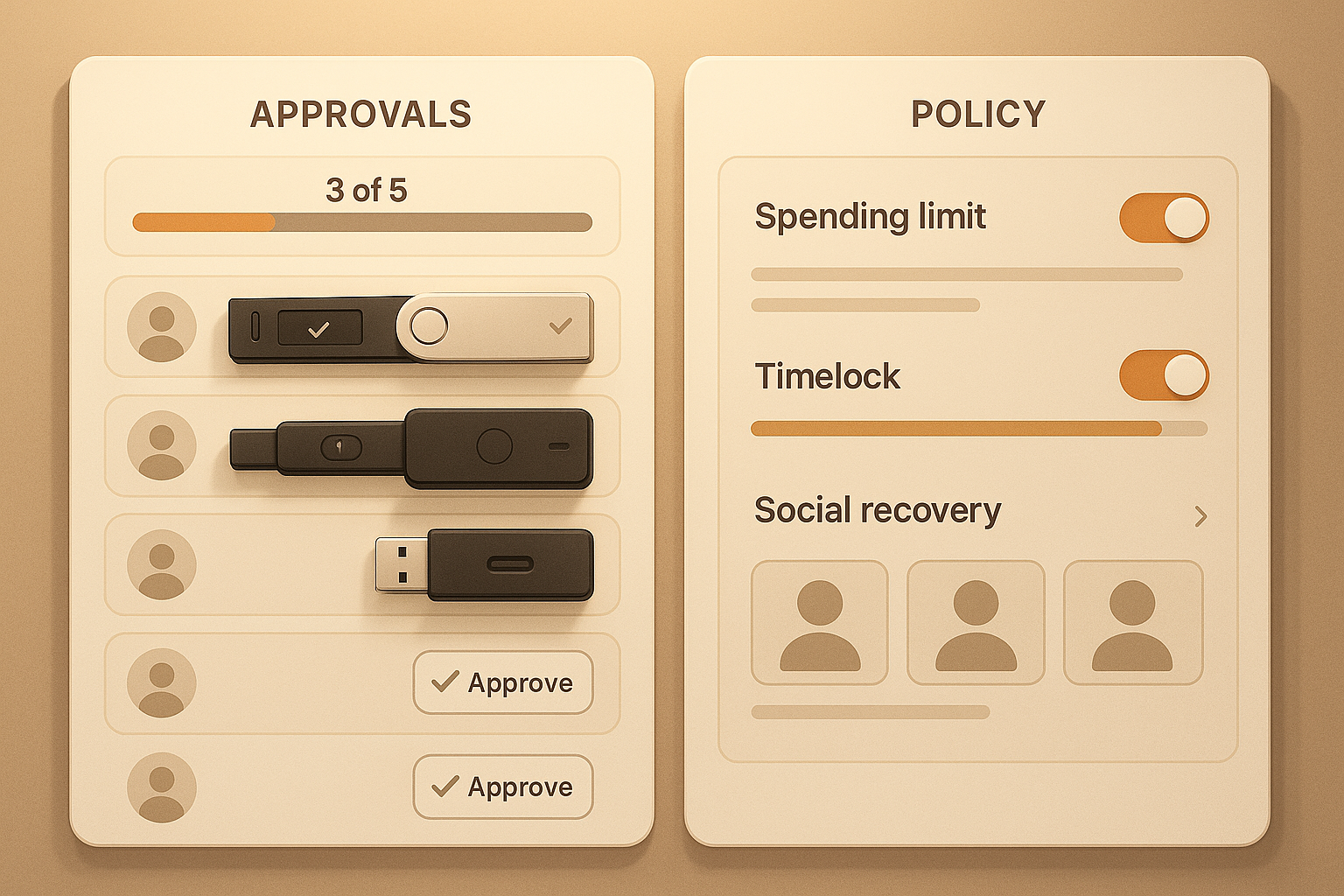
2. How Approvals Work: Static Thresholds vs Programmable Logic
Multisig approvals are straightforward: a proposed transaction collects signatures from authorized keys until it reaches M and then broadcasts. The control is binary—either enough independent keys sign or they don’t. Smart contract wallets evaluate programmatic rules before execution. A policy engine can require multiple approvals and conditions: per-transaction limits, daily spend caps, allowlists/denylists, or even off-chain checks via oracles and APIs. In Ethereum-style SCWs, standards such as ERC-1271 let contracts validate signatures, and account abstraction (ERC-4337) adds a standard flow for submitting “user operations” that contracts evaluate before execution.
How to do it
- Multisig: define N owners, choose M, and specify who can propose and who must co-sign.
- SCW: encode policies: approver roles, limits per token, timelocks, emergency pause, and recovery flow.
- Testing: simulate transactions and rejection paths before funding.
Common mistakes
- Picking M too low (fast but fragile) or too high (safe but unusable).
- In SCW, shipping without a policy for upgrades or without a pause/guard path.
Takeaway: multisig locks on a threshold; SCW lets you express thresholds plus business logic—powerful when you need it, overkill if you don’t.
3. Security Assumptions: Key Hygiene vs Contract Correctness
Multisig security concentrates on key management: keep private keys uncompromised and ensure signers verify what they sign. Attackers must compromise M keys, ideally on segregated devices. In SCWs, correctness expands to contract security: logic bugs, reentrancy edges, upgrade risks, and dependencies (libraries, modules). Both models need sound operational security, but failure modes differ: in multisig, a stolen or phished key is the main concern; in SCW, a vulnerable contract or misconfigured module is equally critical. Tools like OpenZeppelin’s Timelock and Governor patterns can add defense-in-depth to sensitive actions.
Numbers & guardrails
- For teams, prefer hardware keys for at least M signers; no two keys on the same device.
- For SCW, mandate audits for custom modules and require >= 24 h timelocks on admin actions.
Mini checklist
- Multisig: device isolation, anti-phishing signing UX, transaction simulation.
- SCW: audited code, minimal trusted upgraders, runtime guards, and emergency pausing.
Synthesis: multisig risk clusters around people and devices; SCW risk clusters around code and governance—secure both accordingly.
4. User Experience & Recovery: Backup Keys vs Social Recovery
Multisig recovery revolves around replacing a signer or rotating keys; if you lose a key but still meet M, you can spend and reconfigure. For individuals, this can feel heavy—coordinating other signers just to recover. Smart contract wallets enable social recovery: you choose guardians (people or devices) who can help you recover control if you lose your signing key; after a delay, the guardian votes reassign control. Contract wallets can also support session keys—temporary permissions for specific apps—reducing constant pop-ups and improving safety. Account abstraction formalizes these flows, enabling gas-sponsored recovery or off-chain validation hooks. vitalik.eth.limo
Tools/Examples
- Social recovery patterns popularized by community research and AA wallets;
- Session permissions for granular, revocable dapp access without exposing your main key repeatedly.
Common pitfalls
- Too few guardians (single point of failure), or guardians who are hard to reach.
- Ignoring a recovery timelock, which leaves room for stealth takeovers.
Wrap-up: multisig recovers by procedural rotation; SCWs can recover by policy with guardians, often smoother for individuals while preserving strong safety.
5. Cost & Gas: Simple Signatures vs Batched Execution and Sponsorship
On UTXO chains (e.g., Bitcoin), multisig increases transaction size—more signatures, more bytes, higher fee. On EVM chains, multisig often routes through a contract (e.g., Safe), paying gas once the execution triggers; signers co-sign off-chain and execute on-chain when ready. SCWs can batch multiple actions in one transaction and leverage paymasters to sponsor gas or let users pay fees in tokens—improving onboarding when signers don’t hold native coin. Under ERC-4337, users submit UserOperations to an alt-mempool, bundlers package them, and the EntryPoint validates them; paymasters can cover gas under programmable rules.
Numbers & guardrails
- Expect higher calldata for multisig spends with many signers on UTXO chains.
- For SCW, batching reduces overhead when executing multiple calls; a paymaster can sponsor gas, but someone always pays.
Tips
- Simulate execution to estimate gas; keep batched calls small enough to avoid failure.
- For treasuries, budget a monthly on-chain ops cost and monitor spikes.
Conclusion: multisig has predictable costs tied to signatures; SCW can optimize costs via batching and paymasters, but adds moving parts you must monitor.
6. Compatibility & Standards: Bare Keys vs Account Abstraction Primitives
Classic multisig exists across ecosystems: Bitcoin supports m-of-n via script and P2SH/P2WSH, while Ethereum multisig often lives as a contract that records approvals before execution. Smart contract wallets rely on standards that make them interoperate: ERC-1271 for contract signature validation (so apps can treat contracts like “signers”), ERC-4337 for account abstraction flows, and related typed-data signing (EIP-712) for safer, human-readable prompts. These standards ensure dapps recognize SCW signatures and that infrastructure (bundlers, paymasters) can serve them.
Why it matters
- Without ERC-1271, some apps wouldn’t accept contract-based signatures.
- With ERC-4337, SCWs get a common interface for validation and execution.
Mini checklist
- Confirm your target dapps support ERC-1271 and EIP-712 prompts.
- Verify your chain/L2 has robust 4337 infra (bundlers, paymasters).
Key point: multisig is broadly compatible by design; SCW compatibility depends on modern standards that most leading ecosystems now support.
7. Governance & DAOs: Committee Approval vs Modular On-Chain Controls
Multisig naturally supports committee-style approvals: a small group co-signs payments or upgrades. This is common for DAO treasuries and protocol multisigs that act as execution agents. SCWs extend this with governance modules—role-based access control (RBAC), voting, timelocks, and guard contracts that pre-check transactions. For example, Safe supports modules and guards that limit what a module can call and can enforce pre/post checks; OpenZeppelin’s governance patterns combine voting with a TimelockController so sensitive actions queue before execution.
Numbers & guardrails
- For DAO treasuries, pair 3–5 signer multisig with a 48–72 h timelock on admin operations.
- Separate proposer, executor, and canceller roles to reduce correlated risk.
Pitfalls
- Overloading a single module with too much power.
- Skipping well-defined emergency pause pathways.
Summary: multisig is great for small committees; SCW can embed full governance logic—stronger for protocols, provided you keep modules minimal and audited.
8. Permissions & Policy Depth: Thresholds vs Roles, Limits, and Rules
A multisig threshold treats all authorized keys equally unless you run a separate process (e.g., policy doc) off-chain. Smart contract wallets let you encode roles (proposer, approver, executor), spending limits per token, allowlists for destinations, rate limits (daily/monthly quotas), and time delays for risky actions. These features move the policy on-chain, eliminating ambiguity about what is allowed. Many setups use guards to validate parameters and modules to automate repetitive tasks under strict constraints.
How to do it
- Define policy in plain language first; then encode it as roles, limits, and time delays.
- Add a review and simulation step before execution; log and alert on policy denials.
Numbers & guardrails
- Cap high-risk transfers to ≤ 1–2% of treasury per day without extra approvals.
- Require dual approval for contract upgrades and address-book changes.
Takeaway: multisig gives equal signers and a single threshold; SCW lets you build least privilege directly into your wallet.
9. Chain Support & Interoperability: UTXO Script vs EVM Modules and Beyond
Multisig is native to Bitcoin via script types (P2SH/P2WSH) and widely supported by wallets and hardware devices. On EVM chains, multisig is typically implemented via Safe-like contracts, which are de facto standards for teams. Smart contract wallets thrive on EVM thanks to composability and standards; newer designs exist on other chains too. When going cross-chain, ensure your multisig or SCW setup is supported by your target chain/L2 and that relayers/bundlers and paymasters operate there if you rely on account abstraction features. For Bitcoin, remember that address formats and signer limits differ between legacy P2SH and SegWit P2WSH.
Region-specific notes
- Some custodians or auditors require specific address formats (e.g., P2WSH).
- Some L2s have emerging 4337 infra—validate reliability before committing treasury flows.
Mini checklist
- Confirm hardware wallet support for your multisig type.
- Confirm dapp compatibility with SCWs on your chain/L2.
In short: multisig is universal; SCW depth is richest on EVM—plan deployments where tooling and standards are mature.
10. Incident Response: Rotation, Timelocks, Pauses, and Upgrades
When a signer is compromised in a multisig, you can rotate that key by replacing the owner set; in the meantime, the attacker still needs M total signatures to spend. For SCWs, you should design timelocks on critical actions and an emergency pause to stop malicious calls while you patch or upgrade. If your SCW is upgradeable, restrict upgrader roles and require multisig-level approvals plus a timelock so stakeholders can review changes before they take effect. OpenZeppelin’s timelock and governance examples demonstrate robust patterns for queuing and executing sensitive operations with delays.
Numbers & guardrails
- Pause immediately on confirmed compromise.
- Require ≥ 24 h timelock for upgrades; ≥ 48–72 h for protocol-level changes.
- For multisig, maintain documented rotation steps and test them quarterly with a tiny balance.
Pitfalls
- Infinite upgrade power in one address.
- Timelocks that can be bypassed by unguarded delegatecalls or modules.
Summary: multisig incident response is about key rotation and quorum; SCW response is about pauses, timelocks, and safe upgrades—plan both before you need them.
11. Performance & Throughput: Human Latency vs Batched Automation
Multisig throughput is often gated by human coordination—waiting for M signers across time zones. You can streamline with pre-agreed signing windows and notification bots, but the threshold still requires people to act. SCWs can batch actions and delegate automation to modules that execute under strict rules, increasing throughput without sacrificing policy. With account abstraction, bundlers collect user operations and submit them efficiently; paymasters can reduce friction where users lack native gas. Still, automation demands careful guardrails to avoid unintended mass actions.
Tips
- Reserve multisig for fewer, larger transfers and set signing SLAs.
- Use SCW modules for recurring payments, streaming salaries, or periodic rebalancing under limits.
Mini case
- A DAO paying 200 contributors monthly can execute one batched SCW call that pulls from a whitelist and caps per-address amounts; the same in multisig would mean dozens to hundreds of discrete proposals and signatures.
Bottom line: multisig optimizes for deliberate control; SCW can optimize for safe throughput when policy is well-specified.
12. Choosing the Right Tool: A Simple Decision Framework
You don’t choose a wallet—you choose a risk model. If your main risk is single-key compromise and your policy is simple (“pay X vendors, rebalance occasionally”), multisig is ideal. If your risk includes operational mistakes, upgrade risk, onboarding friction, and complex allowances, a smart contract wallet shines. Many teams combine both: a SCW with rich policy governed by a multisig of human signers at the top. The framework below maps common scenarios to a default choice; always test with small amounts before scaling.
| Scenario | Prefer Multi-Signature Wallets | Prefer Smart Contract Wallets |
|---|---|---|
| Small team treasury, < 10 signers | 3-of-5 or 2-of-3 for simplicity | Add SCW only if you need limits/timelocks |
| Large DAO or protocol admin | Use as governance signer of record | Encode timelocks, RBAC, upgrade controls in SCW |
| High-frequency payments | Human latency can bottleneck | Batch and automate with modules/limits |
| New user onboarding | Keys are straightforward but fragile | Social recovery and gas sponsorship reduce friction |
| Cross-app integrations | Works but policy is off-chain | On-chain allowlists, per-app permissions |
Mini checklist
- Risk: loss/theft vs logic bug—what’s more likely for you?
- People: how many approvers, and how available are they?
- Policy: do you need limits, delays, or per-app rules?
- Tooling: does your chain support the modules/standards you need?
Synthesis: pick the simplest model that fully expresses your risk and policy. Start small, document procedures, and iterate as your needs evolve.
Conclusion
Multisig and smart contract wallets both deliver strong controls, but they optimize different failure modes. Multisig spreads risk across independent keys, resisting single-key compromise and keeping the conceptual model simple and durable. Smart contract wallets move policy on-chain, letting you encode roles, rate limits, timelocks, social recovery, and automation—features that reduce human error and enable scale when designed carefully. The practical path is to start with the simplest configuration that meets your requirements, then add policy depth only where the benefit clearly outweighs complexity. Commit to regular simulations, audits where applicable, and rehearsed incident response so you’re never improvising under pressure. If you align your wallet model to your risks, personnel, and workflows, you’ll get reliable security without sacrificing day-to-day usability. Pick your model, test with small funds, write down the playbook, and review it on a schedule.
FAQs
1) What is a smart contract wallet?
A smart contract wallet is an account controlled by on-chain code rather than a single private key. It can require multiple approvals, enforce spend limits, whitelist destinations, add timelocks, and support social recovery. Because rules are explicit in code, you get programmable policy and better automation. The trade-offs are contract complexity and a need for audits and robust governance.
2) How does a multi-signature wallet differ from a smart contract wallet?
Multisig enforces M-of-N approvals from distinct keys—no approvals, no spend. SCW enforces policies written in code—multi-approvals plus rate limits, time delays, and more. Multisig reduces single-key risk with minimal moving parts; SCW reduces operational and UX risk by encoding rules directly on-chain.
3) Is one strictly more secure than the other?
Neither is universally “more secure.” Multisig concentrates risk in key hygiene and signer behavior; SCW concentrates risk in code correctness and governance. Many teams combine both: a SCW with strong policy under the control of a small multisig to approve upgrades and emergency actions.
4) Do smart contract wallets work everywhere?
They work best on EVM chains and L2s that support standards like ERC-1271 and ERC-4337. On other ecosystems, feature parity varies; verify that your target dapps recognize contract signatures and that bundler/paymaster infrastructure is reliable if you plan to use account abstraction features.
5) What is social recovery and who should be a guardian?
Social recovery lets designated guardians help you regain control if you lose your key. Good guardians are people or devices you can reliably reach and trust not to collude—think a hardware key you keep off-site, a colleague, and a dedicated recovery service. Add a delay so you can cancel malicious recovery attempts.
6) What are paymasters and why should I care?
Paymasters are contracts that can sponsor gas for users under conditions—useful for onboarding or letting users pay fees in tokens. They improve UX, but they add dependencies and require funding and monitoring. Someone always pays; ensure you understand the economics before relying on sponsorship.
7) How many signers should my multisig have?
For small teams, 2-of-3 or 3-of-5 balances resilience and usability. Larger groups might adopt M-of-7 to M-of-15. Too few signers increases single-key risk; too many signers slows operations. Model your worst-case availability (e.g., holidays, travel) and set M accordingly.
8) Can smart contract wallets be upgraded? Is that safe?
Many SCWs are upgradeable, which enables fixes and features but introduces governance risk. Restrict upgrader roles, enforce timelocks, and require multi-party approval for upgrades. Consider making core logic immutable if your policy rarely changes; keep only guard or module layers adjustable.
9) Which is cheaper to operate?
It depends on chain, transaction size, and behavior. Multisig spends can be larger on UTXO chains due to more signatures, while SCWs on EVM can batch calls to save gas. If you use paymasters, costs shift to the sponsor. Simulate your common flows to compare real costs before committing.
10) Will dapps recognize my smart contract wallet’s signatures?
Most modern dapps that support ERC-1271 validation will recognize SCW signatures. If an app only supports EOAs, it might require workarounds. Check for ERC-1271 support and prefer dapps that render EIP-712 messages so approvers can read what they are signing.
11) What happens if a multisig signer disappears?
If your threshold still meets M, the remaining signers can rotate ownership and replace the missing signer. If your threshold no longer meets M, funds may be stuck; design quorum with realistic availability, and practice rotations with a small balance so you’re confident under pressure.
12) Can I migrate from multisig to a smart contract wallet later?
Yes. Many teams start with a multisig and later move to an SCW as complexity grows. Plan a staged migration: deploy the SCW, test batched calls and policy, transfer a small float, and expand once you’ve validated real-world operations. Keep the old multisig as a fallback until you’re fully confident.
References
- EIP-4337: Account Abstraction Using Alt Mempool, Ethereum Improvement Proposals. Published Sep 29, 2021. https://eips.ethereum.org/EIPS/eip-4337
- Account abstraction overview, ethereum.org. Published Oct 6, 2025. https://ethereum.org/roadmap/account-abstraction/
- ERC-1271: Typed signature validation for contracts (overview), EIPs / ethereum.org. Published Sep 12, 2017. https://eips.ethereum.org/EIPS/eip-712 (typed data standard related to contract signing UX); ERC-1271 explainer (independent), Jason Stanley. Published Dec 21, 2024. https://jasonstanley.id/blog/erc1271-explained
- Bitcoin: Securing your wallet (multisignature), bitcoin.org. Publication date not stated on page. https://bitcoin.org/en/secure-your-wallet
- BIP-16: Pay to Script Hash, bips.dev. Published Jan 3, 2012. https://bips.dev/16/
- BIP-11: M-of-N Standard Transactions, bips.dev. Published Oct 18, 2011. https://bips.dev/11/
- BIP-67: Deterministic P2SH Multisig (public key sorting), bips.dev. Published Feb 8, 2015. https://bips.dev/67/
- Safe Docs: Smart account modules and guards, docs.safe.global. Published Oct 10, 2025. https://docs.safe.global/advanced/smart-account-modules and https://docs.safe.global/advanced/smart-account-guards
- OpenZeppelin Timelock & Governance Contracts, OpenZeppelin Docs. Publication date not stated on index pages. https://docs.openzeppelin.com/contracts/5.x/governance and https://docs.openzeppelin.com/defender/guide/timelock-roles
- Paymasters in ERC-4337, docs.erc4337.io. Publication date not stated on page. https://docs.erc4337.io/paymasters/index.html