Decentralized systems let you move value and information without a central operator—but they don’t remove accountability. Regulatory challenges of decentralization and blockchain are the recurring legal, compliance, and supervisory hurdles that arise when permissionless, borderless networks meet jurisdiction-bound rules. In plain terms: regulators care about consumer protection, market integrity, financial stability, tax compliance, data rights, and national security; decentralization changes the “who,” “where,” and “how” of those responsibilities. This article unpacks the 11 most common hurdles and shows you how to navigate them without sacrificing the advantages of open networks. Because this touches financial, legal, and security domains, treat the guidance as educational—not legal advice—and consult qualified professionals for decisions that affect your organization.
Quick answer: The core regulatory challenge is attribution—identifying which entity (if any) meets obligations traditionally placed on intermediaries. At a glance, your workflow is:
- Classify the token and activity.
- Map the licensing/registration perimeter you may fall into.
- Implement AML/KYC controls and Travel Rule processes where required.
- Design custody, disclosures, and market surveillance aligned to applicable regimes.
- Document governance, data/privacy design, and cross-border compliance decisions.
Done well, this approach reduces surprises, speeds approvals, and lets you ship products that survive scrutiny.
1. Token classification & legal status
The first and most consequential question is what your token is, legally. This is the lever that determines disclosure requirements, market rules, custody options, and who supervises you. Many regimes begin by asking whether the token looks like a security (an investment tied to others’ efforts), a commodity or utility (functional access or settlement medium), or a payment/e-money instrument (redeemable at par). Decentralization complicates this because the facts are fluid: a network may be centralized at launch, more decentralized later, and different jurisdictions can reach different classifications from the same facts. A pragmatic approach is to define clear token purposes, rights, and distribution mechanics, and to build a living dossier that tracks changes over time so you can show your work to regulators and partners.
Mini table: tests & categories (simplified)
| Regime/Test | What it checks | Practical implication |
|---|---|---|
| “Investment contract” analysis | Expectation of profit from others’ efforts | If met, treat as a security: disclosures, restrictions, venue rules |
| MiCA-style categories (e.g., asset-referenced, e-money, other crypto-assets) | Redemption rights, reserve backing, issuer accountability | Triggers issuer obligations, white papers, reserve/claim rules |
How to approach it
- Write the token story: purpose, holder rights, how value accrues (or not), who can change parameters, and upgrade paths.
- Document distribution: allocations, vesting, any form of public offering, and marketing language that might create profit expectations.
- Design for the target regime: if payment-like, prioritize redemption, reserves, and clarity on claims; if utility-like, minimize profit-forward messaging.
- Plan for migration: define milestones for decentralization; reassess classification at each milestone.
Numbers & guardrails
- Keep marketing copy free of implicit yield language unless you intend to comply with securities-style disclosure.
- If your distribution touches thousands of retail users across multiple countries, assume multi-jurisdictional filings or notifications may be needed.
- Build a classification memo and update it at each material change to protocol control, token economics, or marketing.
Synthesis: Classification is not a one-time verdict; it is a moving picture. Treat it as a governance process and you reduce downstream friction everywhere else.
2. Licensing and the regulatory perimeter
Even if you never issue a token, running an exchange, order book, wallet service, or fiat on/off-ramp can put you inside a licensing perimeter. Many jurisdictions regulate virtual asset service providers (VASPs) or crypto-asset service providers, covering custody, exchange, transfer, advice, and issuance. Decentralization blurs lines: code may be permissionless, but the moment you operate a front-end, set fees, custody keys, provide order routing, or market a service, you can be treated as an intermediary. Your task is to identify where you cross the line from “software” into “regulated service” and either seek authorization or design out the regulated feature.
How to map your perimeter
- List all user touchpoints: custody, order handling, fiat rails, staking-as-a-service, token issuance, or lending.
- Trace money flows: who collects fees, who holds client assets, and who can halt or reverse transactions.
- Spot regulated verbs in your jurisdiction(s): “operate a trading platform,” “custody client assets,” “arrange deals,” “transmit value,” “issue redeemable tokens.”
- Decide: apply for the license, partner with an authorized entity, or modify the product so you’re outside the perimeter.
Tools/Examples
- Authorization frameworks that cover exchanges and custodians tend to require fit-and-proper management, capital, internal controls, compliance officers, and reporting.
- Payment-oriented tokens often fall under payment/e-money style regimes with redemption and reserve conditions.
Synthesis: Perimeter analysis is less about labels and more about functions. Describe what you actually do in verbs—and design your operating model around those verbs.
3. AML/KYC & the Travel Rule in a pseudonymous world
Anti-money-laundering (AML) and counter-terrorist-financing (CTF) regimes expect firms to identify customers, monitor transactions, and share originator/beneficiary data when transferring value between service providers (the “Travel Rule”). Decentralization challenges this because users can hold their own keys and move funds peer-to-peer without an intermediary. The practical result is a split architecture: VASPs must collect and exchange data for transfers between them, screen wallets, and build risk-based controls for interactions with self-custody wallets. Many regimes set a low monetary threshold for enhanced data sharing and treat linked transactions as a single transfer to prevent structuring.
How to do it
- Segment flows: VASP↔VASP (full Travel Rule), VASP↔self-hosted (collect/screen to risk-based standard), self-hosted↔self-hosted (no VASP obligations, but still relevant for investigations).
- Integrate Travel Rule providers and message formats; design fallbacks when counterparties can’t receive data.
- Screen everything: addresses, counterparties, and transaction patterns; block or escalate hits.
- Prove ownership of self-hosted wallets where appropriate (signing challenge, micro-transfer) without collecting excess data.
Numbers & guardrails
- Typical thresholds for originator/beneficiary data sit around the equivalent of 1,000 in major currencies; multiple smaller transfers that appear linked are usually treated as one.
- Build positive proof routines (e.g., signed message) and negative screens (e.g., sanctions lists, mixer proximity) before release of funds.
- Keep Travel Rule messages synchronized with settlement to avoid reconciliation gaps.
Synthesis: AML in decentralized finance is about context. When you can’t rely on account identity, you compensate with counterparty due diligence, behavioral analytics, and robust Travel Rule plumbing.
4. Cross-border conflicts and jurisdiction
Blockchains are borderless, but law is not. You may be incorporated in one country, operate infrastructure across several, serve users in dozens, and settle value on a global network. Jurisdiction can be asserted by the location of users, servers, developers, corporate entities, or even marketing. Conflicts arise when one country treats a token as a security, another as a commodity, and a third as a payment instrument—each with different rules on disclosure, promotions, custody, and tax. The job is not to find a magical “global compliance”; it’s to choose priority markets, tailor the product to those regimes, and geofence or vary features where necessary.
Region notes
- EU-style frameworks emphasize issuer obligations, reserve and redemption rules for payment-like tokens, and broad market-abuse surveillance.
- U.S.-style frameworks often focus on securities-law analysis, broker/dealer or exchange definitions, money transmission, and prudential custody for advisers.
- APAC hubs commonly emphasize licensing of digital payment token services, AML/CTF obligations, and retail protection safeguards.
Numbers & guardrails
- Create a market matrix: columns for target jurisdictions; rows for licensing, marketing/financial promotions, custody, market-abuse, and tax.
- Maintain country-specific risk acceptances approved by leadership for any gaps (e.g., feature toggles, user eligibility, limits).
Synthesis: Cross-border design is a product problem. Ship market-specific configurations instead of pretending one build fits all.
5. Stablecoins & payment rules
Stablecoins expose you to payments law, reserve management, disclosure, and sometimes prudential oversight. Regulators care about redeemability, reserve quality, and operational resilience. If you issue or integrate a stablecoin, expect questions about par redemption, where reserves are held, attestations/audits, concentration risk, and wind-down plans. Some regimes carve out e-money-like tokens with issuer duties; others set guardrails for asset-referenced tokens pegged to baskets. For integrators, obligations may include due diligence on issuers, segregation of client token balances, and clear disclosures about redemption pathways.
How to build it right
- 1:1 backing and clarity on claims: what the holder can redeem, who redeems, and in what time frame.
- High-quality reserves: cash and short-dated instruments at reputable institutions; concentration limits; daily reconciliation.
- Operational resilience: multi-signer controls, key-management, and incident response for de-pegs and chain halts.
- Disclosures users actually read: reserve composition, redemption rules, fees, and exceptions.
Numbers & guardrails
- Keep a meaningful share of reserves in immediately available instruments; publish regular reserve attestations.
- Stress-test redemption queues (e.g., model simultaneous redemptions equal to a significant fraction of float) and define escalations.
- For integrators, set counterparty limits on stablecoin issuers and automatic circuit-breakers for abnormal price deviations.
Synthesis: Stablecoins are payments infrastructure with a balance sheet attached. Treat them with payments-grade controls, not just protocol-grade code.
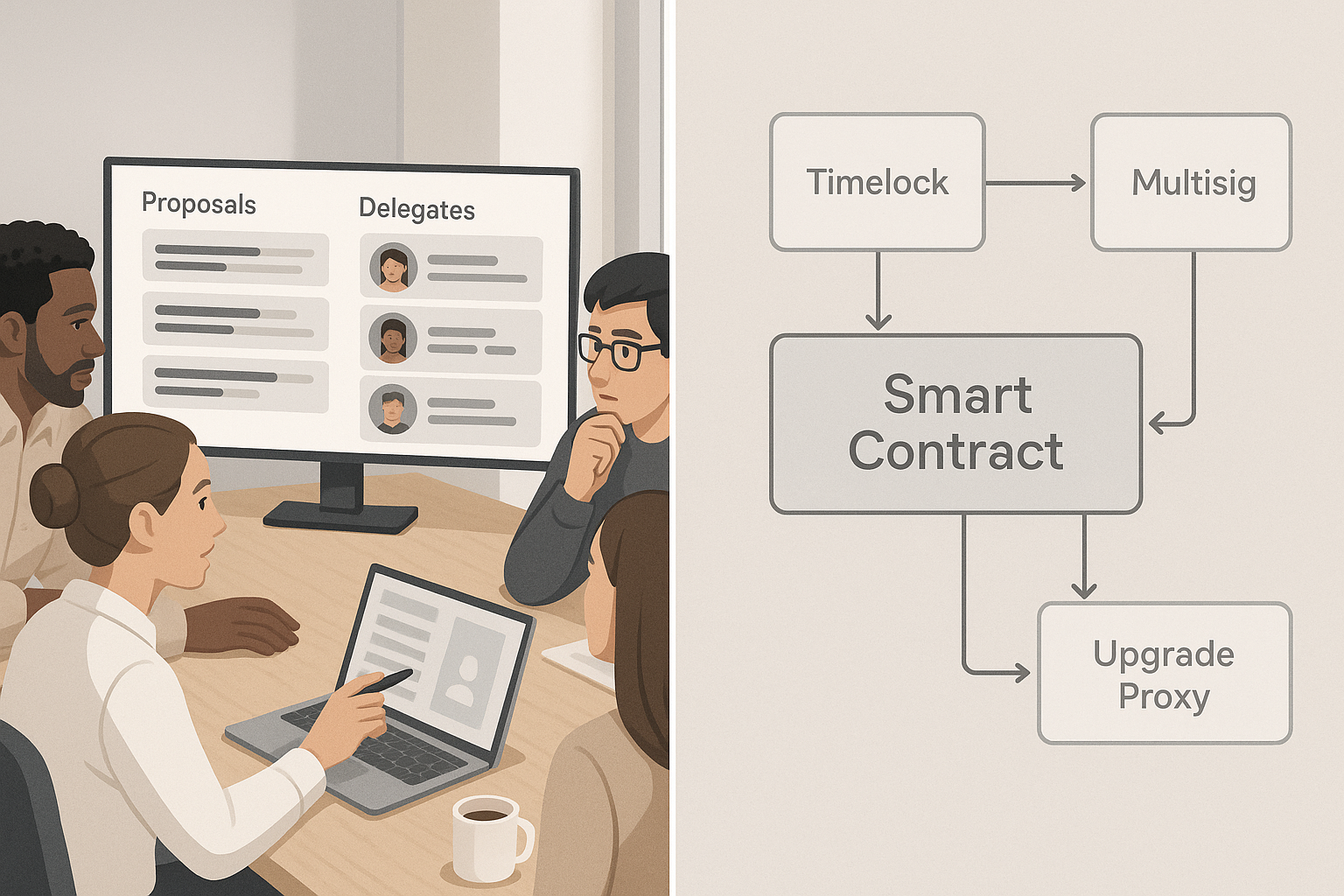
6. DeFi accountability & the “who is the intermediary?” problem
Decentralized finance (DeFi) aims to minimize intermediaries, yet someone writes the code, runs the website, sets fees, and can upgrade smart contracts. Regulators look to these practical levers to identify a responsible party. If your DAO controls admin keys or upgrade multisigs, or if a core team operates a front-end and markets a protocol, expect obligations similar to a service provider—even if the base contracts are permissionless. The hard part is aligning credible neutrality with real-world safeguards like kill-switches or emergency pauses.
How to make accountability work
- Map control surfaces: contracts (ownership, upgradeability), front-ends, oracles, fee switches, admin keys, and governance processes.
- Document roles: core devs, foundation, labs company, DAO committees, delegates; who pays whom; who can change what.
- If you run a front-end, implement onboarding, geo-controls, wallet screening, and disclosures; consider a separate, regulated wrapper for operational roles.
- If you’re truly hands-off, remove admin powers or place them behind time-locked, multi-party governance with clear emergency procedures.
Mini case
A protocol starts with a 5-of-9 multisig that can pause markets and change parameters. To balance safety and decentralization, it (1) narrows the scope of pause powers to market-level, (2) enforces a 24–48 hour time-lock on non-emergency upgrades, and (3) publishes incident-response playbooks with thresholds (e.g., loss estimates, oracle divergence) for when to act.
Synthesis: Decentralization is not the absence of responsibility; it’s the distribution of it. Make the distribution explicit and you’ll withstand the “who is the intermediary?” test.
7. Custody, safekeeping & segregation of client assets
Custody is where law meets key management. If you hold or control client private keys, you take on duties to segregate assets, reconcile balances, manage keys securely, and return assets on demand. Some regimes require that client assets be separately accounted for on-chain and on internal ledgers, disallow commingling with corporate funds, and set standards for qualified custodians. On the tech side, you’ll choose between cold storage, MPC (multi-party computation), or HSM-based approaches and design processes for withdrawal approvals, incident response, and proof-of-reserves (if you publish them).
Practical checklist
- Segregation: unique on-chain addresses or robust sub-ledgering; daily reconciliations; independent operations and finance sign-off.
- Key strategy: cold/hot splits, MPC quorum (e.g., 3-of-5 or 5-of-7), hardware protections, and key-ceremonies with witnesses.
- Withdrawal controls: velocity limits, address whitelists, behavioral analytics, four-eyes approvals.
- Disclosures: who the legal custodian is; what happens in insolvency; whether you rehypothecate (best practice: don’t).
Numbers & guardrails
- Keep hot-wallet exposure to a small single-digit percentage of client assets; enforce per-asset velocity caps.
- Require out-of-band confirmations for large withdrawals and mandatory cool-downs for newly added addresses (e.g., 24 hours).
- If publishing proof-of-reserves, pair it with proof-of-liabilities and describe limitations plainly.
Synthesis: Custody is not solved by cryptography alone. Treat it as an operational discipline with finance-grade controls—and document everything.
8. Market integrity, disclosures & surveillance
Even in crypto, rules against insider trading, market manipulation, and misleading promotions apply. Listing tokens without due diligence, letting insiders trade ahead of announcements, or tolerating wash trading erodes trust and invites enforcement. Where regimes cover crypto markets explicitly, expect white paper or disclosure obligations, financial promotions rules for marketing, and surveillance expectations for venues. Decentralization complicates who’s responsible, but if you run an order book, a router, or a front-end, you should act like a market operator.
How to raise the bar
- Pre-listing review: circulating supply, token unlocks, vesting schedules, governance powers, protocol dependencies, and conflicts of interest.
- Promotions governance: plain-language risk summaries, banned phrases, and a sign-off workflow for campaigns and influencer deals.
- Surveillance: screen for wash trades, layering/spoofing, cross-venue manipulation; investigate and sanction repeat offenders.
- Incident comms: structured channels and timelines for disclosures around exploits, de-pegs, or material governance changes.
Numbers & guardrails
- Consider cooling-off periods for insiders and listing partners; set blackout windows around token unlocks or governance votes.
- Establish price-move triggers (e.g., ±10–20% in short windows) for alerts and manual reviews, tuned per asset liquidity.
Synthesis: Market integrity is mostly process: diligence, surveillance, and clear communication. Build these muscles early and your listings, liquidity, and user trust improve together.
9. Data protection, privacy & identity in immutable ledgers
Blockchains are append-only, which collides with data protection principles like data minimization and erasure. Personal data can appear on-chain through names or addresses—but also through pseudonyms if they can be linked to a person. Your design choices around what goes on-chain versus off-chain matter more than any compliance memo. Put only what must be on-chain; hash or reference sensitive data off-chain; encrypt what you can; define retention and access controls; and appoint a clear data controller for processing that touches personal data.
How to balance it
- Minimize on-chain: store pointers and proofs, not raw personal data; use salted hashes to prevent easy reversal.
- Define roles: who is the data controller versus processor across your DAO, foundation, or vendors.
- Support data subject requests: design deletion at the edges (front-ends, logs, analytics) and consider key-revocation patterns where feasible.
- Privacy-preserving tech: apply zero-knowledge proofs for selective disclosure where practical.
Numbers & guardrails
- Track and log data flows with a simple data map; set explicit retention windows for off-chain logs and analytics.
- Use separation of duties and least-privilege access for any admin-level data tooling.
- Publish a plain-language privacy notice tailored to your protocol and front-end.
Synthesis: Decentralization does not excuse poor privacy hygiene. Design for data minimization and governance clarity from day one.
10. Taxation & information reporting
Tax authorities treat many crypto transactions like property disposals or income events. That means you have to track basis, proceeds, and character (capital vs. ordinary), and in many places exchanges and brokers must report sales and certain transfers. Staking, airdrops, liquidity mining, and token grants can all create taxable income at various points. For global products, expect cross-border reporting frameworks that harmonize how platforms share data with tax authorities and that set due-diligence rules for identifying reportable users.
What to implement
- Ledgering that works: capture cost basis and proceeds per lot; support FIFO/Specific ID; export statements users can actually file from.
- Event classification: trading, swaps, rewards, grants/vesting, airdrops, interest/fees, wrapped assets, and bridges.
- User lifecycle: collect tax IDs where required, validate statuses, and issue statements by deadlines; capture self-custody movements with clear logic to avoid double-counting.
Numbers & guardrails (mini case)
- Example: buy 1 token at 2,000 in your base currency, pay a 20 fee; basis becomes 2,020. Later sell at 2,800 with a 20 fee; proceeds 2,780, gain 760.
- For staking: if you receive 10 tokens as rewards when fair value is 50 each, you may have 500 of ordinary income; later disposition triggers capital gain/loss from that basis.
- Reporting frameworks commonly require due-diligence and annual reporting by platforms and set XML schemas for standardized file exchange.
Synthesis: Taxes reward teams that invest in clean data and classification. Build tax logic into your product; don’t bolt it on at the end.
11. Sanctions compliance & illicit finance risk
Sanctions rules prohibit dealing with listed persons, jurisdictions, or activities. Open networks mean listed addresses and illicit typologies evolve quickly, and failures can trigger severe penalties. Your program should combine preventive screening, real-time controls, and responsive investigation. Pay particular attention to mixers, bridges, and cross-chain obfuscation, as well as to counterparties known to facilitate ransomware or state-linked activity. Decentralization does not shield you: if you operate a service interface, set fees, or otherwise control access, you are expected to identify and block prohibited activity.
What good looks like
- Policy & playbooks: define prohibited and restricted activity, escalation paths, and block/allow logic.
- Data sources: integrate multiple sanctions and risk-intel feeds; tune heuristics for proximity to known bad actors.
- Controls: blocklisted address checks on deposit and withdrawal; holds for ambiguous cases; risk scoring to drive enhanced due diligence.
Numbers & guardrails
- Set zero-tolerance blocks on direct matches and manual review for near-matches or proximity; define cool-down periods (e.g., 24 hours) for risky patterns.
- For front-ends, add geo-IP controls plus wallet screening; for protocols, publish reference lists and compatible open-source screening modules.
Synthesis: Sanctions compliance is a moving target; combine automated screening with trained analysts and clear decision logs to show regulators you are serious.
Conclusion
Decentralization changes the shape of risk, not the existence of it. Regulators still pursue the same policy goals—consumer protection, market integrity, financial stability, tax fairness, data rights, and national security—but the actors and levers shift when there is no central operator. The practical way forward is to treat compliance as product design: classify your token and activities; decide where you sit relative to the licensing perimeter; implement AML/CTF controls tailored to VASP and self-custody flows; design custody and market-integrity processes like a mature operator; build privacy into your architecture; and instrument tax and sanctions logic from the start. None of this removes the need for legal counsel or engagement with supervisors, but it gives you a credible, auditable foundation to ship with confidence. If you’re about to launch or scale a decentralized product, use the 11 sections above as a build checklist—then schedule a pre-launch review with counsel and your leadership team to lock decisions, document trade-offs, and move forward. Copy-ready CTA: Want a one-page checklist version for your team? Share this guide and turn each section into an internal “go/no-go” control.
FAQs
1) Is decentralization itself regulated?
No. Decentralization is an architectural choice, not a legal category. What regulators look at are activities (custody, exchange, issuance, transfer, advice) and outcomes (consumer harm, market abuse, illicit finance). If your decentralized protocol has an interface, fees, or upgrade controls, the operators around those touchpoints often become the regulated actors. Designing responsibilities explicitly—who runs what—keeps surprises to a minimum.
2) Can a utility token become a security later?
Yes. Classification can change if facts change. For example, a token marketed purely for access can drift into “investment-like” territory if communications begin emphasizing profit opportunities or if central actors’ efforts drive price. A good practice is to maintain a classification memo and re-evaluate at each significant change to governance, tokenomics, or marketing.
3) Do I need a license if I only run a DeFi front-end?
Often you will at least need to meet compliance obligations similar to a service provider, including AML screening, sanctions controls, and financial promotions rules. Whether a formal license is required depends on local definitions (e.g., operating a trading venue, transmitting value, custody). If you collect fees, route orders, or custody, assume a higher likelihood that authorization applies.
4) How should we handle the Travel Rule with self-custody wallets?
Most regimes focus Travel Rule obligations on VASPs; self-custody transfers are outside scope unless a VASP is involved. When interacting with self-custody wallets, many providers apply risk-based measures: wallet-ownership checks, sanctions screening, and enhanced due diligence for high-risk patterns. You still need to exchange originator/beneficiary data for VASP↔VASP transfers.
5) Are stablecoins always e-money?
Not always. Classification turns on redemption rights and reserves. Tokens redeemable at par against a single fiat currency often attract e-money-like rules with issuer obligations; asset-referenced tokens pegged to baskets may have separate categories with their own guardrails. If you are just integrating a stablecoin, your obligations focus on due diligence on the issuer, segregation of client balances, and clear disclosures.
6) Does running a DAO protect contributors from liability?
A DAO is a coordination mechanism, not automatically a legal wrapper. If people or entities perform roles (e.g., operate front-ends, pay salaries, market the protocol), liability can attach to them. Many teams adopt foundations, associations, or limited-liability entities to house functions and sign contracts, while keeping on-chain governance for protocol parameters.
7) How do we reconcile immutable ledgers with data erasure rights?
You avoid the collision by not putting personal data on-chain in the first place. Store proofs and pointers, not raw data; keep personal data off-chain with robust access controls and deletion processes at the edges (web apps, logs, analytics). Clarify who is the data controller for each processing activity and provide practical mechanisms for data subject requests.
8) What counts as market manipulation in crypto?
Classic behaviors still apply: wash trades, spoofing, pump-and-dump schemes, misuse of insider information, and manipulative self-trading to influence price or volume. If you operate an exchange or order router, implement surveillance, alert thresholds, and enforcement playbooks. Disclose token unlocks, vesting, and governance events that materially affect supply or control.
9) Do swaps between tokens trigger taxes?
In many places, yes—swapping one token for another is a disposal for tax purposes. That means calculating proceeds and gains/losses at the time of the swap. Your product should capture cost basis, fees, and dates per lot, and let users export statements that align to local rules. Staking and airdrops can create income at receipt, with separate capital gains on disposal later.
10) Are sanctions programs relevant if we never touch fiat?
Yes. Sanctions apply to persons and activities, not just fiat rails. If you provide a service, operate a front-end, or otherwise facilitate transactions, you must screen and block prohibited counterparties and activity. Use multiple data sources, set clear block/hold policies, and maintain audit trails of decisions and escalations.
11) What’s the fastest way to get “compliance-ready” before launch?
Run a pre-launch sprint: (1) finalize token and activity classification; (2) decide on licensing or partnerships; (3) implement AML/CTF, Travel Rule, and sanctions controls; (4) lock custody architecture and segregation; (5) complete a privacy impact assessment; (6) wire up tax reporting; (7) draft disclosures and incident playbooks. Freeze scope, fix gaps, and document every decision.
References
- Virtual Assets and Virtual Asset Service Providers—Risk-Based Approach Guidance, Financial Action Task Force (FATF), 2019, https://www.fatf-gafi.org/content/dam/fatf-gafi/guidance/RBA-VA-VASPs.pdf
- Best Practices on Travel Rule Supervision, FATF, 2025, https://www.fatf-gafi.org/content/dam/fatf-gafi/recommendations/Best-Practices-Travel-Rule-Supervision.pdf
- Regulation (EU) 2023/1114 on Markets in Crypto-Assets (MiCA), EUR-Lex, 2023, https://eur-lex.europa.eu/eli/reg/2023/1114/oj/eng
- Framework for “Investment Contract” Analysis of Digital Assets, U.S. Securities and Exchange Commission (SEC), 2019, https://www.sec.gov/about/divisions-offices/division-corporation-finance/framework-investment-contract-analysis-digital-assets
- Application of FinCEN’s Regulations to Certain Business Models Involving Convertible Virtual Currencies (FIN-2019-G001), Financial Crimes Enforcement Network (FinCEN), 2019, https://www.fincen.gov/resources/statutes-regulations/guidance/application-fincens-regulations-certain-business-models
- Policy Recommendations for Decentralized Finance (DeFi), International Organization of Securities Commissions (IOSCO), 2023, https://www.iosco.org/library/pubdocs/pdf/IOSCOPD744.pdf
- Prudential Treatment of Cryptoasset Exposures, Basel Committee on Banking Supervision (BIS), 2022, https://www.bis.org/bcbs/publ/d545.htm
- Blockchain and the GDPR: Solutions for a Responsible Use of the Blockchain in the Context of Personal Data, CNIL (French Data Protection Authority), 2018, https://www.cnil.fr/en/blockchain-and-gdpr-solutions-responsible-use-blockchain-context-personal-data
- Guidelines to Notice PSN02—AML/CFT for Digital Payment Token Service Providers, Monetary Authority of Singapore (MAS), 2019, https://www.mas.gov.sg/regulation/guidelines/guidelines-to-notice-psn02-on-aml-and-cft—dpt
- Sanctions Compliance Guidance for the Virtual Currency Industry, U.S. Department of the Treasury, 2021, https://home.treasury.gov/system/files/126/virtual_currency_guidance_brochure.pdf
- Crypto-Asset Reporting Framework (CARF)—FAQs, Organisation for Economic Co-operation and Development (OECD), 2025, https://www.oecd.org/content/dam/oecd/en/topics/policy-issues/tax-transparency-and-international-co-operation/faqs-crypto-asset-reporting-framework.pdf
- Frequently Asked Questions on Virtual Currency Transactions, Internal Revenue Service (IRS), 2019–, https://www.irs.gov/individuals/international-taxpayers/frequently-asked-questions-on-virtual-currency-transactions
- Guidance on Custody or Safekeeping of Customer Virtual Currency, New York State Department of Financial Services (NYDFS), 2023, https://www.dfs.ny.gov/reports_and_publications/press_releases/pr202301231