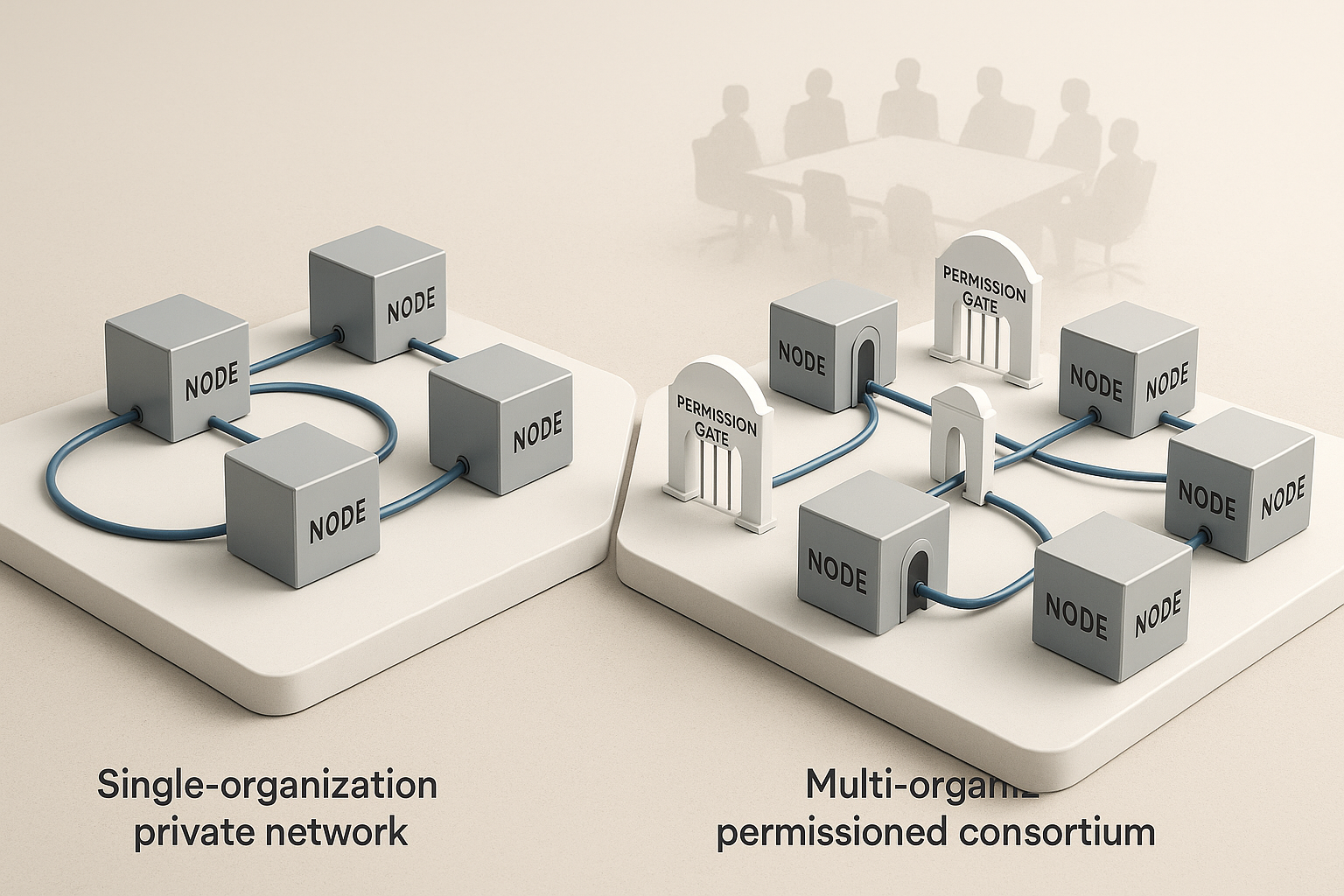
If you’re comparing private vs permissioned blockchain, the core question is not “which is better,” but “which fits your governance, risk, and business objectives.” A private blockchain typically means a ledger controlled by one organization with restricted participation. A permissioned blockchain restricts participation too, but is usually shared across multiple known organizations under a common governance. In one sentence: private focuses on single-owner control; permissioned focuses on multi-party coordination with access controls. To decide quickly, identify your trust boundary, map who runs validator nodes, and align participation rules with real-world contracts and compliance duties. This is not legal or financial advice; for regulated decisions, consult qualified professionals.
Here’s a fast path you can skim now and deepen later: (1) define who must write to the ledger and who must read it, (2) decide whether one or several organizations should run consensus, (3) choose a governance model that matches that reality, (4) select privacy controls for data minimization, (5) test performance with realistic workloads, and (6) budget for operations, upgrades, and onboarding. Done well, you’ll gain faster settlement, cleaner audit trails, fewer disputes, and an integration surface your existing systems can actually maintain.
1. Definitions and Scope: What Each Term Really Means
A private blockchain is best understood as a ledger that one enterprise owns and operates; participation is restricted by the operator, and consensus is typically under that operator’s administrative control. A permissioned blockchain, by contrast, is any ledger where participation—read, write, or validate—requires approval, usually granted by a consortium or governing body representing multiple organizations. Both models restrict access, but they differ in who grants permission and how authority is distributed. In practice, private often equals “permissioned, single operator,” while permissioned often equals “permissioned, multi-operator consortium.” This difference drives governance choices, compliance posture, and the credibility of on-chain records across parties who don’t share an IT department. If you need neutral ground between firms, permissioned usually fits better; if you need an internal audit-grade ledger, private is often enough. Understanding this distinction prevents confusion later in selection, architecture, and procurement.
Why it matters
- Authority distribution: Private centralizes control; permissioned distributes it across known members.
- Credibility with partners: Partners view permissioned ledgers as less biased than private ledgers run by a single counterparty.
- Change management: Updating rules is simpler in private, but multi-party consent in permissioned can build durable trust.
- Risk allocation: Failure domains and operational risk spread differently depending on who runs validator nodes.
- Ecosystem growth: Permissioned networks can onboard new members with clearer, pre-agreed procedures.
Common mistakes
- Treating “private” and “permissioned” as identical and skipping governance design.
- Assuming private automatically means faster or cheaper without workload testing.
- Underspecifying approval workflows for joining, leaving, and sanctioning members.
Synthesis: Anchor your vocabulary early. When everyone agrees on “private” versus “permissioned,” your governance, security, and operational plans snap into focus and avoid costly redesigns.
2. Governance and Membership: Who Decides What, and How
The most important practical difference is governance: private chains centralize decision rights with one organization; permissioned chains distribute decision rights across a consortium. Governance covers membership criteria, voting thresholds, change management, dispute resolution, and sanctions. You’ll codify how new members join, who can run validator nodes, how smart contracts are approved, and how upgrades roll out. A clear charter translates business rules into operational controls: what’s a quorum, which actions need supermajority, and who can freeze or reverse transactions under defined conditions. Without these structures, networks drift into ambiguity, and disputes spill outside the system you’re trying to streamline. Align on governance before you talk technology, so your architecture expresses the operating agreement—not the other way around.
How to do it
- Draft a charter: Define membership classes (operator, validator, observer), rights, and obligations.
- Set thresholds: Specify voting ratios for upgrades, onboarding, offboarding, and emergency actions.
- Define enforcement: Establish penalties for misbehavior and a process for evidence and appeals.
- Pin legal identity: Map on-chain identities to legal entities and real-world signatories.
- Plan exits: Document data handover, node shutdown, and continuity when a member leaves.
- Publish change logs: Keep transparent records of approved changes and rationales.
Numbers & guardrails
- Quorum: Many consortia pick a two-thirds supermajority for protocol changes to balance agility and safety.
- Membership growth: Plan for dozens of organizations, even if you start with a handful; onboarding shouldn’t require a redesign.
- Role limits: Cap any single member to ≤ 33% of validators to avoid de facto control in practice.
Synthesis: Sound governance turns “permissioned” from a buzzword into operational trust. For one-organization needs, a private chain’s simpler governance can be a feature; for multi-party markets, shared governance is the product.
3. Consensus and Security: Threat Models You Actually Have
Private blockchains typically optimize for fault tolerance and auditability under one operator, while permissioned blockchains must withstand collusion risks among several independent organizations. The question isn’t only “which consensus is faster,” it’s “which consensus assumes the right adversary.” In a private setting, threats are insider misuse, system misconfiguration, and key management lapses. In a permissioned setting, add incentives for a subset of members to stall or censor. Choosing consensus mechanisms like crash-fault tolerant (CFT) or byzantine-fault tolerant (BFT) should reflect who might cheat, how many could collude, and what evidence you need post-incident. Don’t over-index on theoretical maxima; model how your actual participants behave, and what it takes to detect and prove bad behavior.
Tools/Examples
- CFT (e.g., Raft): Faster under benign assumptions; adequate when members share an operator or legal umbrella.
- BFT (e.g., IBFT, BFT-Smart, PBFT-style): Tolerates some malicious validators; useful when independent firms co-run validators.
- Hardware security modules (HSMs): Reduce key-theft risk for validators and signers.
- Audit trails: Append-only logs off-chain to correlate with on-chain events for forensic readiness.
Numeric mini case
- Validators: With 4 validators and BFT consensus, you can tolerate 1 malicious validator (f = ⌊(n−1)/3⌋).
- Censorship: If 1 out of 5 validators controls block proposals, define rotation and slashing policies to bound stall time.
- Keys: Rotate signing keys at least once per quarter-equivalent cycle of your organization’s policy to limit blast radius.
Synthesis: Choose consensus to match the adversary you actually face. Private chains can lean on CFT and controls; permissioned consortia often justify BFT and stronger misbehavior proofs.
4. Performance and Scalability: Throughput, Latency, and Workload Fit
Private networks often post lower latency because one operator optimizes hardware, networking, and batching. Permissioned networks introduce cross-org cryptography, more signatures, and governance checks, which add overhead. Still, both models can achieve thousands of transactions per minute under realistic enterprise conditions when workloads are batched and smart contracts are efficient. The real performance storyline is not a single “TPS number” but how throughput scales with more organizations, more complex contract logic, and stricter privacy. Plan for end-to-end performance, including API gateways, event delivery, and downstream databases that index ledger state for applications. Benchmark using representative payload sizes, realistic endorsement policies, and real network latencies instead of lab-perfect loops.
Numbers & guardrails
- Latency: Sub-second commit in private CFT is common; 1–3 seconds in permissioned BFT with 5–7 validators is a typical planning target.
- Throughput: With 1–2 kB transactions and batched commits, 2,000–5,000 tx/min is a reasonable envelope on commodity cloud nodes.
- Payloads: If payloads exceed 128 kB, store hashes on-chain and objects off-chain to avoid bloating blocks.
- Endorsements: Each additional endorser adds signature verification cost; start with 2 and scale only when risk demands it.
How to test it
- Replay real traffic: Use anonymized historical messages or synthetic data with matching size and variance.
- Profile contracts: Measure CPU and I/O hotspots; simplify logic and pre-validate inputs.
- Tune batches: Adjust block size and timeouts to your arrival patterns.
- Measure E2E: Include API, queueing, indexing, and downstream writes in your SLA calculations.
Synthesis: Both models can meet demanding enterprise workloads when engineered thoughtfully. Size your throughput and latency to business SLAs—not to a vanity TPS figure.
5. Privacy and Data Controls: What You Reveal and To Whom
Private blockchains inherit privacy from centralized administration; data stays within one organization’s boundary, with access enforced by IAM and database policy. Permissioned blockchains need more nuanced controls because multiple organizations see a shared ledger; not every transaction should be visible to every member. Techniques include per-channel partitioning, private data collections, role-based encryption, and selectively sharing state proofs instead of full payloads. For sensitive records—payments, health, or identity—limit on-chain data to minimal, non-identifying facts, keep PII off-chain, and use hashes or commitments to prove integrity. The goal is to minimize data exposure while still getting the benefits of a jointly verifiable system of record that shortens audits and speeds reconciliation.
How to do it
- Data minimization: Put only necessary fields on-chain; keep bulky or sensitive data off-chain with a hash pointer.
- Selective disclosure: Use channels, collections, or ACLs so only involved parties see details.
- Key management: Separate encryption keys per organization and rotate regularly.
- Proofs over payloads: Share zero-knowledge-style attestations or Merkle proofs when details aren’t needed.
- Right to erasure: Store personal data off-chain so deletion requests operate on primary stores, not immutable blocks.
Numeric mini case
- PII footprint: Moving 90% of a customer profile off-chain while anchoring 10% (non-identifiers + hashes) can cut breach exposure drastically while preserving auditability.
- Retention: If your legal team mandates 7-year-equivalent retention, implement off-chain lifecycle policies; ledger anchors need not contain personal data.
- Access: Limit full-payload visibility to parties directly involved; everyone else gets proofs only—often reducing data distribution by > 70%.
Synthesis: Private chains achieve privacy through central control; permissioned chains achieve it through design. Use minimization and selective disclosure to keep verifiability without oversharing.
6. Compliance and Legal Fit: Controls That Survive Audit
Compliance is about demonstrating that your controls work, not just asserting that they exist. Private blockchains map cleanly to internal control frameworks and policies already familiar to auditors. Permissioned blockchains must also satisfy cross-organization obligations: data protection, records management, financial controls, and sector-specific rules. Treat the ledger as an evidence machine: every change is attributable, ordered, and tamper-evident. The art is deciding what not to put on-chain so you can fulfill deletion, retention, and localization duties without heroic exceptions. Document how identities on-chain relate to legal entities off-chain, and show that governance enforces this mapping continuously, not only at onboarding.
Region notes
- Data localization: Keep personal or sensitive data in-region; anchor proofs on-chain; replicate nodes only where allowed.
- Deletion vs immutability: Delete off-chain source data; keep non-identifying anchors on-chain to preserve integrity.
- Financial records: Mirror existing segregation-of-duties controls through endorsement policies and role separation on validator nodes.
- eDiscovery: Index transaction metadata off-chain so legal holds and searches are practical.
Numeric mini case
- Audit cycles: If you face quarterly internal audits, design role-based reports that export evidence in minutes, not weeks.
- Retention tiers: Segment records into policy buckets (e.g., 2, 5, 7 years-equivalent) off-chain, and link them via stable identifiers to on-chain anchors.
- Segregation of duties: Require at least 2 endorsements from distinct organizations for any high-risk contract update.
Synthesis: Map compliance obligations to design choices early. Private aligns with internal audits; permissioned requires shared evidence and jointly enforced controls.
7. Cost and Total Cost of Ownership: What You’ll Actually Pay
Cost depends on node count, consensus type, privacy features, and the humans who operate the system. Private blockchains centralize operations and can be cheaper at small scale because one team runs everything. Permissioned blockchains spread cost across members, but add coordination overhead: more meetings, change management, and multi-party testing. Cloud VMs, storage, bandwidth, HSMs, monitoring, support, and incident response all contribute. The biggest hidden cost is governance time for design and upgrades; budget for it explicitly. Avoid false economies like under-spec’d nodes or skipping disaster recovery; the first incident will erase those “savings.” Model TCO over multiple planning horizons with realistic growth and onboarding rates.
Numbers & guardrails
- Nodes: A starter private network might run 3–5 validator/peer nodes; a permissioned consortium might run 2–3 per member across 5–10 members.
- Compute: Commodity cloud instances often suffice; reserve burst capacity for reindexing and major upgrades.
- Storage: Plan ledger growth at x10 your daily write volume over your policy horizon to cover indexes and metadata.
- Ops staffing: Private: 1–3 FTEs; Permissioned: shared across members, but expect coordination hours per release.
Mini checklist
- Include onboarding costs per new member (keys, nodes, contracts, tests).
- Price HSMs and key ceremonies for validators and signers.
- Budget observability (logs, metrics, tracing) equal to app spend; it pays for itself at the first incident.
- Negotiate SLAs with any managed service to match your business hours and incident severity ladder.
Synthesis: Private looks cheaper up-front; permissioned shares cost as you scale participants. TCO clarity comes from modeling humans, not just machines.
8. Integration and Identity: Making It Work With What You Already Have
A blockchain that doesn’t integrate is a project plan waiting to disappoint. Private blockchains plug into your existing identity and access management (IAM) stack, logging, and APIs with fewer organizational hurdles. Permissioned blockchains integrate across multiple organizations, so you’ll translate identities from each member into agreed on-chain representations and align them with legal entities. Integration patterns include REST or gRPC APIs, event streams to downstream systems, and off-chain databases that index state for analytics and reporting. You’ll also coordinate maintenance windows, API versioning, and schema evolution that avoid breaking other members’ integrations. Establish a common identity standard so business rules tie cleanly to real people and firms, and use standardized attestations when you can to prevent bespoke glue code.
How to do it
- Federate identity: Map corporate IAM (e.g., OIDC/SAML) to on-chain identities; define attribute assertions for roles.
- Event-driven design: Emit events for state changes; consumers update their systems idempotently.
- Schema governance: Version smart-contract schemas; publish migration guides; deprecate predictably.
- Reference adapters: Provide SDKs or connectors to ERP/CRM so members don’t reinvent plumbing.
- Secrets & keys: Keep app keys in vaults; automate rotation and least privilege for services and humans.
Numeric mini case
- Latency budget: If your downstream commit takes 300 ms, allocate ≤ 50 ms for signature verification per call and ≤ 100 ms for contract execution to stay under a 1 s app SLA.
- Throughput: If partners need 1,200 events/min, partition consumers and buffer with queues sized for 5 minutes of burst.
Synthesis: Private chains integrate like any internal platform. Permissioned chains succeed when identity and event contracts are standardized across members—and when adapters make adoption boring.
9. Interoperability and Standards: Avoiding Dead Ends
Interoperability matters when your ledger must exchange proofs, assets, or identity claims with other systems. Private blockchains usually interoperate via enterprise integration patterns within one organization, while permissioned networks benefit from standards that help members (and their partners) connect future systems without custom bridges. Favor open standards for decentralized identifiers and credentials, consider cross-chain messaging frameworks prudently, and keep assets abstracted from any one platform. The aim is substitutability: you can change one component without rewriting your entire stack. When the network’s value depends on third-party adoption, interoperability is not a “later” item—it is a day-one requirement.
Tools/Examples
- Decentralized identifiers and verifiable credentials: Standardize how entities prove attributes across domains.
- Cross-chain messaging: Use carefully, only where security and finality models align.
- Proof formats: Commit to portable proof objects (hashes, Merkle proofs, signatures) rather than platform-specific payloads.
- Schema registries: Publish contract schemas so external systems can validate messages consistently.
Mini checklist
- Define proof exchange formats early and test with at least 2 independent implementations.
- Document trust assumptions for any bridge; avoid bridging assets if finality models diverge.
- Keep vendor-neutral identities and credentials to reduce platform lock-in.
Synthesis: Private chains can live happily inside your stack. Permissioned consortia need standards to grow beyond the founding members without glue code sprawl.
10. Operations, Reliability, and Risk Management: Keeping the Lights On
Operations make or break credibility. Private blockchains concentrate operational duties: monitoring, alerting, backups, key management, and incident response under one team. Permissioned blockchains multiply coordination: each member must meet baseline SRE practices so the network doesn’t inherit the weakest participant’s downtime. Define SLOs for availability and recovery, practice disaster scenarios, and automate upgrades with rollback paths. Instrument everything: node health, block propagation, smart-contract metrics, and end-to-end latencies. Treat key ceremonies and validator rotation as routine, not rare; the more muscle memory, the less drama. When incidents happen—and they will—respond with blameless postmortems that fix processes and tooling, not just people.
Numbers & guardrails
- Availability: Plan for 99.9% service SLOs at the application layer; validate dependencies so your ledger isn’t the only reliable component.
- Backups: Snapshots at hourly intervals plus off-site storage; test restores regularly.
- Disaster recovery: Define RPO/RTO targets; rehearse failover between regions with realistic data volumes.
- Key rotation: Rotate validator and app keys on a predictable cadence; automate certificate renewal to avoid surprise expirations.
Common mistakes
- Treating ledger nodes as “set and forget” servers.
- Upgrading smart contracts without a rollback or feature flag path.
- Skipping incident-response practice across member organizations.
Synthesis: Private operations are centralized; permissioned operations require shared discipline. Reliability is what earns trust after launch day.
11. Decision Framework and Business Use Cases: Picking With Confidence
Choose private when one organization must own operations, move quickly, and satisfy internal audit with minimum coordination. Choose permissioned when independent organizations need a shared source of truth, equal voice in governance, and jointly verifiable records. Map decisions to business outcomes: reduce reconciliation time, accelerate settlements, harden audit evidence, and enable new market structures like shared registries or multiparty workflows. Then prove your choice with a pilot scoped to a single product line or region and expand only after operational maturity. You don’t need to “boil the ocean”; you need a specific, valuable lane where distributed trust pays for itself and scales predictably as more members join.
Business patterns
- Private shines for: Internal asset tracking, compliance logging, audit trails, and long-lived workflows inside one enterprise.
- Permissioned shines for: Trade finance consortia, supply chain traceability across brands, multiparty KYC sharing, and shared registries.
- Hybrid patterns: Keep sensitive data private; anchor proofs and shared references on a permissioned ledger.
Numeric mini case
- Reconciliation: A shared permissioned ledger that replaces email-and-spreadsheets can cut dispute cycles from weeks to days with automated status proofs.
- Onboarding: Designing standard adapters can reduce partner integration time from months to weeks, compounding as each new member reuses the same kit.
- Audit: A private chain for internal controls can cut evidence-gathering man-hours by > 50% through deterministic logs and automated exports.
Synthesis: Tie architecture to outcomes and prove it with a small, high-value pilot. If trust crosses enterprise boundaries, permissioned earns its cost; if trust stays inside, private is often enough.
Conclusion
The phrase private vs permissioned blockchain only makes sense when anchored to governance, security assumptions, and the business outcomes you need. Private blockchains centralize control and streamline operations for one enterprise, excelling at internal audit trails and deterministic workflows. Permissioned blockchains distribute control across known organizations, excelling at neutrality, shared evidence, and multi-party automation where trust must be built rather than assumed. Both models demand careful choices about privacy, performance, and integration, and both reward teams that treat governance and operations as first-class design inputs. If you define who is allowed to participate, set clear decision thresholds, minimize on-chain data, and instrument the full path from API to analytics, you’ll end up with a platform that your auditors, partners, and developers all trust. The right next step is small and concrete: pick one process, one set of partners, and one measurable metric—and deliver a pilot that proves the fit. Ready to choose? Write down your must-have outcomes and map them to the eleven factors above, then draft your governance one-pager today.
FAQs
1) Is a private blockchain always permissioned?
Yes. Private implies restricted participation controlled by one organization, which is a form of permissioning. The confusion comes from using “private” for single-operator networks and “permissioned” for multi-operator consortia. Clarify terms early so technical choices match governance reality.
2) When is a permissioned blockchain overkill?
If all parties already trust one operator, or if a relational database with append-only logs and strong IAM meets audit requirements, a permissioned consortium may add cost without new value. In those cases, a private ledger or even a hardened database may be the simpler, faster choice.
3) What consensus should I pick for a consortium?
Choose a byzantine-fault tolerant mechanism when independent organizations run validators, because it tolerates a minority acting maliciously or failing independently. If one operator effectively controls validators, a crash-fault tolerant approach with strong internal controls may suffice.
4) How do I reconcile immutability with data deletion rights?
Keep personal data off-chain and store only non-identifying anchors on the ledger. When deletion is required, erase the off-chain record while the on-chain anchor remains as proof that a record existed without revealing personal details. This pattern balances integrity with privacy obligations.
5) Can we mix private and permissioned models?
Yes. Many architectures are hybrid: individual firms keep sensitive data in private ledgers or databases and anchor proofs, shared references, or asset registries in a permissioned network. This lets you control exposure while benefiting from multi-party verification.
6) What are the biggest cost drivers we should plan for?
Human time for governance, onboarding, and coordinated testing is the largest hidden cost, followed by infrastructure for validators, storage growth, and observability. Budget for key management (including HSMs), backups, and disaster-recovery exercises; they pay back at the first incident.
7) How do we prove compliance to auditors and regulators?
Treat the ledger as an evidence factory: deterministic logs, attributable signatures, clear identity mappings, and reproducible reports. Document endorsement policies, key rotations, and change approvals. Export reports automatically so evidence assembly takes minutes, not weeks of manual work.
8) What privacy techniques should we use with multiple organizations?
Combine data minimization with selective disclosure. Use channels or collections so only involved parties see full details, and share proofs (hashes or Merkle proofs) with the rest. Keep PII off-chain and encrypt sensitive off-chain stores with per-organization keys and rotation policies.
9) How do we onboard new consortium members smoothly?
Publish a technical onboarding kit: identity requirements, key ceremony steps, reference adapters, test vectors, and a certification checklist. Run a sandbox network where new members can validate their setup before touching production, and schedule joint drills to practice upgrades and incident response.
10) What if a member misbehaves or goes offline?
Your charter should define thresholds for sanctions, removal, and emergency actions. BFT consensus helps tolerate a limited number of faulty or malicious validators. Complement with monitoring, slashing-like penalties in contracts, and legal remedies aligned to the governance agreement.
11) Which industries benefit most from permissioned networks?
Industries with complex, multi-party workflows and high compliance burden: supply chains, trade finance, capital markets post-trade, health data exchanges, and verifiable identity ecosystems. The shared ledger reduces reconciliation cycles, clarifies responsibilities, and creates audit-ready evidence across firms.
References
- Hyperledger Fabric Documentation, The Linux Foundation. https://hyperledger-fabric.readthedocs.io/en/latest/
- GoQuorum Documentation, Consensys. https://consensys.net/docs/goquorum/
- Corda Documentation, R3. https://docs.r3.com/corda/
- NIST Privacy Framework, National Institute of Standards and Technology. https://www.nist.gov/privacy-framework
- ISO/TC 307 Blockchain and distributed ledger technologies, International Organization for Standardization. https://www.iso.org/committee/6266604.html
- Decentralized Identifiers (DID) v1.0, World Wide Web Consortium. https://www.w3.org/TR/did-core/
- Data protection rules as a pillar of citizens’ empowerment and the EU’s approach to the digital transition, European Commission. https://commission.europa.eu/law/law-topic/data-protection_en
- Enterprise Ethereum Alliance Specifications, Enterprise Ethereum Alliance. https://entethalliance.org/specifications/