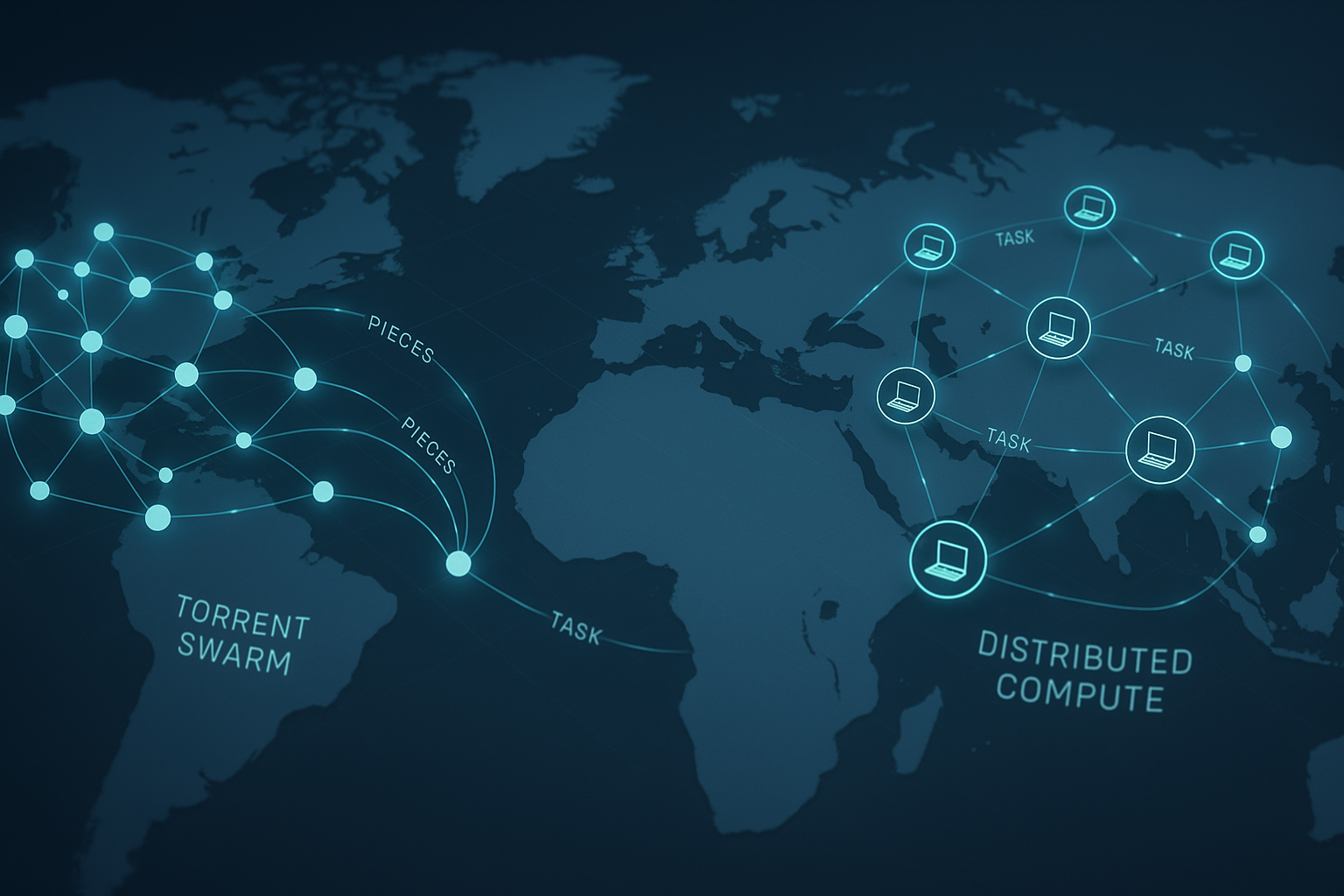
Peer-to-peer networks are systems where participants both consume and provide resources—bandwidth, storage, or compute—without relying on a single central server. In torrent swarms and distributed computing, this architecture spreads load, improves resilience, and scales elastically with demand. At a glance, peer-to-peer networks work by letting peers discover each other, exchange small units of data or work, verify integrity, and adapt to changing conditions like churn and congestion. In plain terms, a P2P system replaces a single warehouse with a marketplace where everyone can both shop and sell.
Quick answer: A torrent swarm uses a content identifier (like a hash) to find peers via trackers or DHT, downloads the file in pieces from many sources at once (swarming), and verifies each piece cryptographically. A distributed computing network assigns tasks to many volunteers, aggregates results, and cross-checks integrity. To design or tune one, you: pick an overlay (often DHT), define content addressing, plan chunk sizes and swarming policy, combine tracker and trackerless discovery, handle NAT traversal, design incentives, secure integrity, choose availability/consistency trade-offs, schedule compute fairly, manage resource limits, observe swarm health, and set legal/ethical guardrails.
If your use case touches copyright, privacy, or security, apply local law and organizational policy, and consult qualified professionals. You’ll find the 12 pillars below, each with steps, mini-examples, and guardrails you can apply immediately.
1. Overlay Topology & DHT Fundamentals
A robust P2P network starts with how peers find things and each other. The most common design uses a Distributed Hash Table (DHT) as the overlay: a key–value map spread across peers that maps content IDs to peer locations. In torrent ecosystems, the widely used DHT follows the Kademlia design, which organizes peer IDs in a space where “distance” is computed with XOR; lookups route through progressively closer nodes and complete in logarithmic steps. The key benefit is scalable, decentralized indexing: no single server must know everything, and failures are survivable because many nodes share responsibility. In practice, this means floods of file or task requests can be absorbed organically as the network grows, rather than collapsing a central index. Kademlia’s bucketed routing tables (k-buckets) keep fresh contacts and prune dead ones, which is vital in the presence of churn.
Why it matters
- Scalability: DHT lookups resolve in about log₂(N) steps; doubling participants increases hops marginally.
- Resilience: No single point of failure; nodes can join/leave without crashing the index.
- Cost: Peers donate indexing capacity; operators avoid big centralized hosting bills.
How it works
- Pick a 160-bit or 256-bit ID space.
- Assign IDs via hashing; store (key → peer list) mappings.
- Use XOR distance; route queries to peers “closer” to the target key.
- Maintain k-buckets per distance range; refresh them periodically.
Numbers & guardrails
- Latency budget: Expect ~log₂(N) overlay hops; with 100,000 nodes, a typical bound is ≈17 overlay steps; parallel queries reduce wall-clock time.
- Routing table hygiene: Keep k-buckets populated; prune unresponsive peers promptly to keep lookup times predictable.
Synthesis: Choose a mature DHT (e.g., Kademlia) for discovery and indexing so peers can always find content or tasks quickly, even as the network grows and churns.
2. Content Addressing & Magnet Links
To route to the right data without a central directory, P2P systems address content by what it is rather than where it lives. Torrents identify payloads by a cryptographic hash (the info hash), enabling magnet links—compact URIs that contain just enough to discover a swarm and fetch metadata from peers, no .torrent file required. The magnet’s xt parameter (eXact Topic) carries the content identifier, while optional tr parameters seed initial trackers. Content addressing also powers systems like IPFS, where CIDs (Content Identifiers) point to immutable content; once you know the CID, any peer holding those bytes can serve them. This decouples data from hosts, supports offline-first workflows, and prevents “link rot” when locations change. Wikipedia
How to apply it
- Use magnet links for distribution: magnet:?xt=urn:btih:<hash>&tr=<tracker-url>.
- In content-addressed stores (e.g., IPFS), generate a CID per object; pin important data.
- Treat the content hash as the primary index key across your P2P services.
Mini example
- A 1.2 GiB dataset is published via xt=urn:btih:<160-bit hash>.
- Peers bootstrap from one tr= URL or via DHT; they fetch metadata (piece list) from peers, then begin swarming the payload.
Numbers & guardrails
- Hash lengths: BitTorrent v1 uses a 160-bit hash; newer schemes may use 256-bit multihashes for stronger collision resistance.
- Security: If integrity is mission-critical, sign or publish hashes in a trusted channel (e.g., your organization’s site or a signed catalog).
Synthesis: Use content addressing and magnet links to make your identifiers durable and location-independent; this eliminates central catalog bottlenecks and simplifies distribution.
3. Swarming & Chunking Strategy
P2P performance hinges on how you slice the file/work and how pieces propagate. Torrents split payloads into fixed-size pieces (e.g., 256 KiB–4 MiB) and often request the rarest pieces first to maximize diversity and avoid “last piece” stalls. Smaller pieces improve parallelism but increase protocol overhead (more metadata, more hash checks). Larger pieces reduce overhead but can underutilize peers on slow links. Distributed compute follows a similar logic: break workloads into work units large enough to amortize scheduling overhead yet small enough to load-balance across heterogeneous devices.
How to tune chunk size
- Start point: For broadband swarms, 512 KiB–2 MiB pieces balance overhead and throughput.
- Compute tasks: Aim for units that run in a few minutes on commodity CPUs/GPUs to keep turnaround tight.
- Metadata size: Remember the piece list grows with smaller pieces; keep .torrent/metadata feasible for quick transfer.
Mini case: piece math
- For a 1 GiB file:
- With 512 KiB pieces, you have ~2,048 pieces (fast rarest-first mixing, more hash checks).
- With 2 MiB pieces, you have ~512 pieces (less overhead, slower mixing on small swarms).
- Choose based on expected peer counts and link quality.
Common mistakes
- Using tiny pieces on high-latency links (excess chatter).
- Using giant pieces in small swarms (poor parallelism).
Synthesis: Set piece/work-unit sizes to balance overhead with parallelism so swarming stays smooth from the first byte to the last.
4. Peer Discovery: Trackers vs. Trackerless (DHT, PEX, LSD)
Peers need introductions. Trackers are centralized services that hand out fresh peer lists; they’re fast and simple but add a dependency. Trackerless discovery uses the DHT to look up peers by info hash, and Peer Exchange (PEX) lets peers gossip new contacts. On local networks, Local Service Discovery (LSD) piggybacks on multicast to find neighbors quickly—great for lab, campus, or office scenarios. A resilient design typically uses both: bootstrap with one or two trackers for fast starts, then rely on DHT/PEX/LSD to sustain growth and heal peer graphs during outages.
How to do it
- Bootstrap: Publish at least one tracker URL; also seed the info hash into DHT.
- Stay decentralized: Enable PEX so peers propagate contacts.
- Go local: Turn on LSD where multicast is allowed to keep on-LAN traffic on LAN.
Numbers & guardrails
- Maintain a peer set window (e.g., dozens to low hundreds) to avoid connection storms.
- LSD and PEX reduce external bandwidth usage; DHT avoids total reliance on trackers.
Synthesis: Combine trackers for fast starts with DHT/PEX/LSD for steady-state resilience—so discovery continues even if a tracker blips. bittorrent.org
5. NAT Traversal & Reliable Connectivity
Most peers sit behind NATs and firewalls. To connect them, you need STUN to learn public reflexive addresses, ICE to try connection candidates in priority order, and TURN as a relay fallback if direct paths fail. Torrent ecosystems add UDP hole punching and purpose-built extensions so two “inbound-blocked” peers can still meet. The rule of thumb: attempt direct UDP/TCP first (lowest latency and cost), punch holes where possible, and relay only when necessary. This layered approach maximizes successful connections and mitigates the long-tail of restrictive NATs.
How to do it
- Use ICE to gather candidates (host, reflexive via STUN, relayed via TURN), then connect using the best that works.
- Enable UDP hole punching in clients that support it (where safe and permitted).
- Keep lightweight keepalives to maintain NAT bindings without flooding the network.
Numbers & guardrails
- Expect direct paths to win when at least one side has an open port; otherwise, punch or relay.
- TURN adds extra hops; reserve it for cases where direct connectivity fails to keep latency predictable.
Mini example
- Two peers behind typical home NATs: each queries STUN, they attempt direct UDP to each other, and, if blocked, fall back to a TURN relay; data flows either way with integrity and congestion control preserved.
Synthesis: Treat STUN/ICE/TURN and hole punching as a progressive ladder from direct to relayed paths, maintaining high success rates without sacrificing performance.
6. Incentives, Tit-for-Tat & Seeding Strategy
Healthy swarms motivate contribution. BitTorrent’s choking/unchoking logic implements a tit-for-tat-ish strategy: upload to peers who upload to you, plus an optimistic unchoke to discover new opportunities. This aligns incentives: if you upload, you download faster; if you don’t, you risk being deprioritized. In compute networks, incentives can be credits, recognition, or access to results. The goal is the same—align individual behavior with collective performance.
How to tune it
- Upload slots: Limit concurrent uploads for stable TCP/UDP performance.
- Optimistic probes: Periodically test a new peer to avoid lock-in and discover better partners.
- Seeding policy: Encourage seeding after completion to improve availability and handle late joiners.
Mini case: simple ratio
- If each finisher seeds to a ratio of 1.0 (uploads as much as they download), the swarm’s replication factor quickly grows, making late arrivals complete smoothly even if original seeders disconnect.
Common mistakes
- Over-aggressive slot counts (thrashing).
- Disabling optimistic unchoke (stagnant peer graph).
Synthesis: Use tit-for-tat-style reciprocity with gentle exploration so your swarm rewards contribution and continuously finds better throughput paths.
7. Integrity, Verification & Transport Choices
P2P thrives on trustless verification. Torrents verify each piece with a hash; metadata lists piece hashes so clients can detect corruption immediately. Many systems adopt Merkle trees, allowing partial verification and resumable downloads. For transport, classic TCP is simple and reliable, while uTP (a UDP-based protocol) adds LEDBAT congestion control to back off when it senses delay, protecting other traffic like video calls or browsing. Whether you use TCP, uTP, QUIC, or a mix, integrity checks remain non-negotiable—every piece must validate before it’s shared onward.
Tools/Examples
- BEP 3: Defines peer wire protocol and piece verification.
- BEP 29: uTP with LEDBAT to yield to interactive traffic.
Numbers & guardrails
- Piece rechecks: Re-hash failed pieces immediately; blacklist misbehaving peers.
- Latency impact: uTP/LEDBAT reduces queueing delay under load; expect smoother concurrent use on shared links.
Synthesis: Combine robust cryptographic verification with congestion-aware transports so data remains correct while coexisting politely with other network traffic.
8. Consistency, Availability & Partition Trade-offs (CAP)
In open networks, partitions happen: peers vanish, links flap, and the overlay reforms. The CAP lens says you can’t guarantee strong consistency and full availability under partition; you must choose trade-offs. Torrent distribution favors availability and partition tolerance with eventual consistency of metadata and piece availability—perfect for immutable payloads. Distributed compute often needs result correctness over instantaneous availability, so it leans toward stronger verification and quorum acceptance. Designing your system means deciding where you can accept stale views and where you can’t, then tuning retries, backoff, and validation accordingly.
Numbers & guardrails
- Metadata tolerance: Immutable payloads simplify consistency (hash is the ground truth).
- Quorums: For compute verification, consider redundant assignment (e.g., 2–3 replicas) and accept a result on majority agreement.
Mini checklist
- Decide if your data is mutable or immutable.
- Choose AP (torrent-like) or CP (result-quorum-like) tendencies for each data path.
- Document time-to-consistency and failure modes plainly.
Synthesis: Make explicit CAP choices per pathway (discovery, data, results) so your P2P behavior under failure is predictable and safe for users.
9. Distributed Scheduling for Volunteer Compute
Distributed computing turns idle devices into a “community supercomputer.” A scheduler parcels work units, sends them to volunteers, validates returned results (often with redundancy), and aggregates outputs. Systems in this space separate control (project servers) from execution (volunteers) and design for heterogeneity: different CPUs, GPUs, memory sizes, and online windows. Effective scheduling balances fairness (don’t starve slow hosts) with throughput (feed fast ones). The architecture excels for embarrassingly parallel tasks like parameter sweeps, image processing, and search problems.
How to do it
- Work unit design: Encode inputs + deterministic procedure; define acceptable runtime bounds.
- Redundant validation: Assign the same unit to multiple volunteers; accept majority-agreeing results.
- Credit & reputation: Reward accurate, timely returns to promote reliability.
Mini case: throughput math
- 10,000 work units × 3 minutes each = 30,000 compute-minutes.
- With 1,000 active volunteers averaging 2 concurrent tasks, wall time is roughly 15 minutes, ignoring variance and queue overhead.
Synthesis: Partition tasks, validate results redundantly, and schedule adaptively so many small contributions add up to big, trustworthy compute.
10. Resource & Load Management (Bandwidth, Connections, Backpressure)
More isn’t always better. Opening hundreds of connections can thrash the OS and reduce throughput per stream. Likewise, unlimited upload floods queues, starving interactive traffic. Successful P2P nodes implement connection caps, rate limits, and backpressure—only requesting or uploading as fast as the slowest link can sustain. Congestion-sensitive transports (uTP/LEDBAT) and request pipelining further smooth usage. The aim is high delivered goodput (verified bytes or completed tasks per second), not just high instantaneous bandwidth.
Practical guardrails
- Connection window: Keep active connections in the dozens to low hundreds, not thousands.
- Upload slots: Fix small concurrent upload slots; expand cautiously as bandwidth allows.
- Shaping: Prefer transport-layer congestion control over crude, static rate caps when possible.
Mini checklist
- Track piece re-requests as a quality signal—spikes indicate overload or bad peers.
- Monitor queue depth and RTT; back off when both rise together (bufferbloat warning).
Synthesis: Shape demand to network reality so each peer remains a good citizen while maintaining high overall swarm throughput.
11. Observability & Swarm Health Metrics
What you don’t measure you can’t improve. In torrents, track availability (how many distinct copies of each piece exist), churn (join/leave rate), replication factor, time-to-first-byte (TTFB), end-to-end completion time, and bad-piece rate. In compute, monitor result validation failure, turnaround time, and host reliability. Visualizing these across time helps you spot weak trackers, DHT pockets, throttling, or a few large seeders becoming overloaded.
A compact checklist table
| Metric | Why it matters | Typical guardrail |
|---|---|---|
| Piece availability | Prevents last-piece stalls | Keep ≥1.5–2.0× copies across swarm |
| Peer set size | Balances parallelism vs. overhead | Dozens–low hundreds active |
| TTFB | Measures discovery + first exchange | Seconds, not minutes, for healthy swarms |
| Bad-piece rate | Flags integrity or hostile peers | Near zero; auto-ban offenders |
| Validation failure (compute) | Ensures correctness | Redundant replicas where needed |
Numbers & guardrails
- Replication: Encourage seeding to sustain ≥1.5× piece replication during peak demand.
- Churn tolerance: Keep discovery diversified (trackers + DHT + PEX + LSD) to survive peer turnover.
Synthesis: Instrument the few metrics that predict user experience so you can act before swarms stall or results degrade.
12. Legal, Ethical & Governance Considerations
Technology is neutral; usage isn’t. For torrents, ensure payloads are lawful for distribution in your jurisdiction and that users understand their device may upload pieces automatically as part of swarming. For compute, be transparent about what code runs, what data leaves the device, and how results are used. Organizations should set policy boundaries (e.g., opt-in only, signed workloads, content classification) and build moderation pathways for abuse reports. If you serve regions with strict privacy rules, minimize personal data, avoid logging IPs longer than necessary, and document your retention practices. When in doubt, capture explicit consent and provide a clear off-switch.
Mini checklist
- Publish a plain-language acceptable use policy.
- Sign torrents/workloads; verify signatures before execution.
- Provide opt-out and data deletion mechanisms.
- Document what metadata is exchanged (e.g., IP addresses, peer IDs) and why.
Synthesis: Build trust with transparency and guardrails so participants benefit from the network without unintended exposure or legal risk.
Conclusion
Peer-to-peer systems thrive by turning every participant into both a client and a contributor. In torrents, that means content addressing, DHT-based discovery, chunked swarming, tit-for-tat incentives, and congestion-aware transports that keep the network friendly. In distributed computing, it means carefully sized work units, redundant validation, and scheduling that treats heterogeneity as a strength. Across both, clarity about CAP trade-offs, thoughtful NAT traversal, disciplined resource limits, and pragmatic observability separate smooth user experiences from stalled swarms and brittle schedulers. If you apply these 12 pillars—overlay design, addressing, swarming, discovery, connectivity, incentives, integrity, consistency choices, scheduling, resource control, observability, and governance—you’ll ship P2P systems that scale gracefully, remain resilient under churn, and respect participants. Start small, measure honestly, and iterate—your swarm will get better every day.
CTA: Use one pillar this week—optimize piece size or enable DHT + PEX—and measure the difference in completion times.
FAQs
1) What’s the simplest way to start a resilient swarm?
Use a tracker and DHT for discovery, publish a magnet link, choose a moderate piece size (e.g., 512 KiB–2 MiB), and enable PEX. This gives you quick starts from trackers and durable operation from the DHT even if the tracker hiccups. Add LSD on LANs to keep local traffic local.
2) How do magnet links differ from .torrent files?
A .torrent file packages metadata (piece list, trackers). A magnet link carries a content hash and optional tracker hints; your client uses that to fetch the metadata from peers (via extensions) and then joins the swarm. It’s lighter to share and more resilient to link rot. GitHub
3) Do I need TURN servers for torrents?
Not strictly, but any P2P that wants maximal connectivity benefits from the STUN/ICE/TURN toolbox. Use direct paths and hole punching first; reserve TURN for restrictive NATs or enterprise firewalls to keep latency and cost in check.
4) What transport should I prefer: TCP, uTP, or QUIC?
Use what your ecosystem supports best. uTP is popular in torrent clients because LEDBAT yields under congestion, protecting interactive traffic. QUIC brings similar benefits with different trade-offs. Whatever you choose, keep integrity checks at the piece layer.
5) How big should my pieces/work units be?
There’s no one size. For files, smaller pieces increase parallelism but add overhead; for compute, target a few minutes per unit to balance scheduling cost and fairness. Pilot with your actual peers and links; adjust to minimize stalls and re-requests.
6) How do tit-for-tat and optimistic unchoke help me?
They reward peers who upload to you and periodically sample for faster partners, preserving fairness and avoiding stagnation. This typically improves overall completion time, especially in mixed-capacity swarms.
7) What’s the difference between DHT and PEX?
DHT is a decentralized lookup table mapping content IDs to peers; it works even if you have no initial contacts beyond bootstrap nodes. PEX is peer-to-peer gossip that shares additional contacts during a session. Use both for robust discovery.
8) How do I validate results in volunteer computing?
Assign the same work unit to multiple volunteers and accept a majority match; give more weight to reliable hosts. Use cryptographic checks and sanity bounds to catch tampering or accidental corruption. Projects like BOINC document practical patterns.
9) Which CAP choice fits torrents?
Torrents lean toward availability and partition tolerance with eventual consistency of metadata and piece presence. Immutable content plus piece hashing makes this safe: you either have the exact bytes or you don’t, and the hash says which.
10) How should I observe swarm health day-to-day?
Track piece availability, peer set size, TTFB, completion times, and bad-piece rates. In compute, monitor validation failure and turnaround time. If availability dips below roughly 1.5× and stalls appear, nudge seeding or troubleshoot discovery.
References
- BEP 3: The BitTorrent Protocol — BitTorrent.org — bittorrent.org
- BEP 5: DHT Protocol — BitTorrent.org — bittorrent.org
- BEP 10: Extension Protocol — BitTorrent.org — bittorrent.org
- BEP 29: uTP (Micro Transport Protocol) — BitTorrent.org — bittorrent.org
- RFC 8445: Interactive Connectivity Establishment (ICE) — IETF Datatracker — IETF Datatracker
- RFC 5389: Session Traversal Utilities for NAT (STUN) — IETF Datatracker — IETF Datatracker
- RFC 5766: Traversal Using Relays around NAT (TURN) — IETF Datatracker — IETF Datatracker
- RFC 6817: Low Extra Delay Background Transport (LEDBAT) — RFC Editor — RFC Editor
- Kademlia: A Peer-to-Peer Information System Based on the XOR Metric — PDOS, MIT — MIT CSAIL PDOS
- Content Addressing & CIDs — IPFS Docs — IPFS Docs
- Discovery & Routing Overview — libp2p Docs — libp2p
- Help Maintain and Develop BOINC — University of California, Berkeley — boinc.berkeley.edu
- Eventual Consistency: Limits and Extensions — ACM Queue — ACM Queue