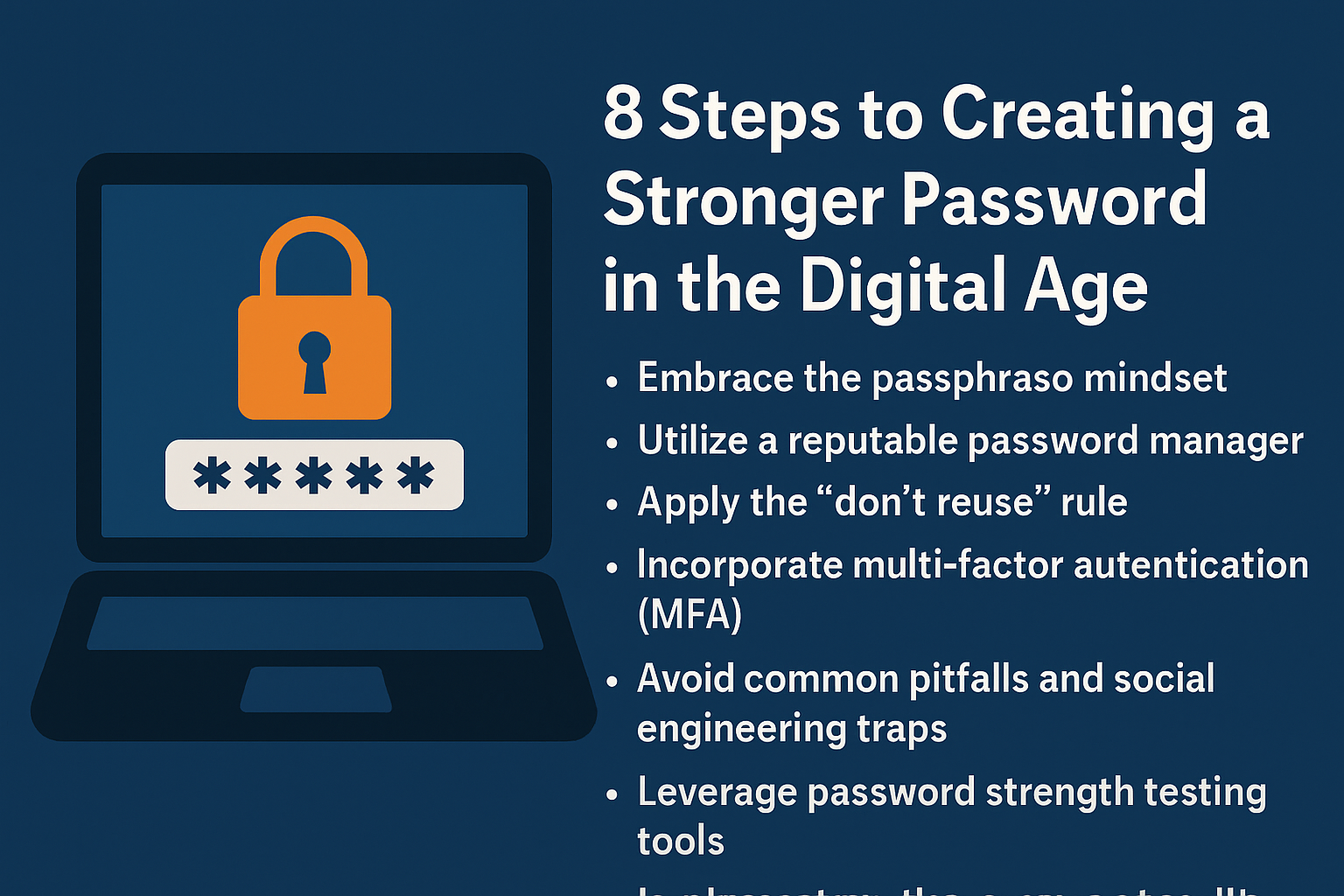
We use the internet for almost everything we do every day, such as banking, shopping, socializing, and getting medical care. You are putting yourself at risk for cyberattacks, data breaches, and identity theft when you create a new account. If you have a weak password, it’s like leaving your front door open for bad people to come in. I’ve worked in cybersecurity for more than ten years, and I’ve seen how bad password habits can hurt both personal and business systems.
It’s not enough to just check “make your password stronger” off your security list. It’s the first line of defense in a battle that is always changing. Digital criminals are always coming up with new ways to steal passwords, like AI-powered password-cracking tools, rainbow tables, and phishing schemes. It’s getting easier for search engines and browsers to find these stolen credentials. But if you follow a structured plan based on proven best practices, you can make your account much safer without making it harder to use. These tips will help you make strong passwords that will keep you safe from modern threats, whether you use the internet a lot or not. Are you ready to take charge of your digital fortress? Let’s get started.
Step 1: Get your mind ready for the passphrase
Why Passphrases Are Better Than Easy-to-Guess Passwords
In theory, passwords that are a random mix of letters and numbers can be strong. But in real life, they don’t always work. People often write them down or use them on more than one site. A passphrase, on the other hand, is a short sentence or a long string of words that is simple to remember. For instance:
“Elephants Dance in the Sun at Midnight!”
- Long (26 characters) means that there are a lot of different ways to put them together.
- Memorable because our brains remember pictures better than random strings.
- It’s hard because of the capital letters, the exclamation mark, and the words that don’t fit together.
The main benefits are:
- Resilience to brute-force attacks: If you add an extra character to a password, it takes about twice as long to crack.
- Less use of symbols: Symbols can make things harder, but they also make it harder to remember passwords. Strong passphrases are long and hard to guess.
- A short sentence is easier to remember than “X7%kL9@zR.”
Step 2: Find a password manager that you can trust
Why You Should Use a Password Manager
It’s hard to keep track of a lot of strong, unique passwords. Password managers are safe apps that make, save, and fill in complicated passwords for you. Some of the best options for encrypting your vault with just one master password are 1Password, Bitwarden, and Dashlane. This means you only need to remember one phrase.
Pros:
- The “one-password-fits-all” problem is solved by using a different password for each site.
- Your computer’s password strength meter can help you make strong passwords.
- Give your family or team members your login information in a safe way.
- You can get to your vault from your computer, phone, or browser extension with cross-platform syncing.
- If you want to be open and have community audits, pick an open-source option like Bitwarden.
- To make your password manager safer, always use two-factor authentication (2FA).
Step 3: Follow the “Don’t Use Again” Rule
The Risk of Using the Same Password Again
If you use the same password for more than one account, it’s like using the same key for your home, car, and office. If a service has a data breach, hackers will try to use your credentials on other sites. This is called “credential stuffing.” The 2024 Verizon Data Breach Investigations Report says that more than 60% of the hacked accounts had weak or reused passwords.
How to stop using again:
- Your password manager can help you make strong passwords.
- There shouldn’t be any confusion if you clearly label your entries, like “Gmail—Personal” and “Gmail—Work.”
- Make sure to check your passwords often: Most password managers have security dashboards that show you which passwords are the same.
Step 4: Add MFA (multi-factor authentication)
Adding MFA to make things more secure
A password can always be broken, no matter how strong it is. Multi-factor authentication adds a second or third level of verification, like:
- SMS codes aren’t as safe because there are attacks that switch SIM cards.
- Apps like Authy and Google Authenticator that help you log in.
- Hardware tokens, like the YubiKey.
- Recognizing a face or a fingerprint are examples of biometric factors.
MFA makes it very hard for people who shouldn’t be able to get in because they need “something you know” (your password) and “something you have” (an authenticator device).
How to make it happen:
- When you can, always use time-based one-time passwords (TOTP) instead of SMS.
- FIDO2 hardware keys could help keep your email, bank, and cloud storage accounts safe from phishing.
- Store your MFA recovery codes in a safe place that isn’t connected to the internet.
Step 5: Don’t make the same mistakes over and over again or fall for social engineering traps
Recognize and Fight Back Against Manipulation
Phishing, smishing (SMS phishing), and vishing (voice phishing) are all common ways for hackers to get people to give them their passwords. They might:
- Send fake emails that look like they come from well-known companies.
- Make fake websites that look like real login pages.
- Act like you’re IT support to “confirm” your credentials.
Take care of yourself:
- Take a close look at the URLs: Make sure the domain is right and starts with “https://.” For example, “paypal.com” instead of “paypai.com.”
- If you want to know where a link in an email or chat will take you, hover over it before you click it.
- Don’t ever give out your password; real businesses won’t ask for it.
- To protect yourself from phishing, use browser add-ons like Avast Online Security or Netcraft.
Step 6: Use tools to see how strong your passwords are
Check the strength of your password.
Check the strength of your new password with a trusted service like Have I Been Pwned’s Password Checker or Dropbox’s zxcvbn (the library that many websites use) before you use it. These tools can tell you how long it would take to guess your password and if it is in big datasets of breaches.
The best ways to do things are:
- Always go to the official site and never type your real password into a field you don’t trust.
- How long and how random a passphrase is are more important than how hard it is to guess.
- Your passwords should be at least this strong. They need to be strong enough to withstand at least one year of brute-force attacks when they are not connected to the internet.
Step 7: Check your passwords often and change them if you need to
Why It’s Important to Check Things Out A lot
When it comes to passwords, you can’t just “forget it.” Your risk profile can change over time as hackers find new ways to break into systems or make tools that let them do it faster. Check your most important accounts every three months:
- Check for passwords that are used more than once.
- Look at notifications of a breach, like those from your email or password manager.
- Change the passwords for your main email, bank account, corporate VPN, and other important services.
Tip for automation: Some password managers can remind you to change weak or old passwords on their own, which makes it easier.
Step 8: Teach Yourself and Your Friends
Getting used to putting “safety first”
What keeps a group or home safe is its weakest link. Make cybersecurity a part of your daily life:
- Teach your family or coworkers how to spot phishing.
- Give people tips on how to protect their personal devices, such as by using screen locks and keeping their software up to date.
- Stay up to date: The National Institute of Standards and Technology (NIST) and the Open Web Application Security Project (OWASP) are two good places to get information.
Letting people know to be careful can help lower the chance that they will make a mistake that makes your strong passwords less secure.
Common Mistakes to Avoid
- Don’t use symbols that you forget to make your passwords too hard.
- Don’t send passwords through email or save them in plain text files.
- Don’t skip installing software updates that fix security holes that let hackers get passwords.
- Don’t rely on just “security questions,” which are often easy to guess or find on social media.
- Don’t think you’re “too small” to be attacked—automated attacks don’t care and scan millions of accounts.
The End
You need to have a good password strategy in the digital world, which is always changing. You can protect yourself from cyber threats by using long, easy-to-remember passphrases, password managers, multi-factor authentication, and regular audits. Don’t forget that the human side is just as important as the technical side. You need to be aware, be on guard, and always be learning. If you don’t use these eight steps all the time and don’t have a proactive attitude, they won’t help you.
Take charge of your life today. Go back to your important accounts and use these tips. Get the people around you to do the same. Using one strong password at a time can make the Internet safer for everyone.
Questions and Answers (FAQs)
- How often do I need to change my passwords?
In the past, it was recommended that you change your passwords every three months. However, new rules (like NIST SP 800-63B) say to only do it if you think your passwords have been stolen or if your password manager tells you to. If you change your passwords too often, they might become weaker and easier to guess. - Are passphrases really safer than passwords that are long and hard to remember?
Yes. A passphrase with 20 to 30 random words usually has more entropy than an alphanumeric password with symbols that is 8 to 12 characters long. You won’t want to write down passphrases as much because they’re easier to remember. - Are managers of passwords safe?
You are the only one who can decrypt your data when you use a good password manager that uses end-to-end encryption. Open-source software like Bitwarden is more trustworthy because people can check its security on their own. - What if a site doesn’t let you use special characters?
Choose length over difficulty if you have to. Make your passphrase longer. If that doesn’t work, use stronger MFA and the longest password that is supported. - Is two-step verification (2FA) enough?
Two-factor authentication (2FA) is a big step up, but for the most important accounts, you might want to use biometric verification or hardware tokens (FIDO2). - Are “security questions” a safe way to get back into your account?
No, most of the time. You can usually find answers to common security questions, like your mother’s maiden name or the name of your first pet, on social media or in public records. If you can, pick questions that aren’t very well known, or skip them and use email, SMS, or two-factor authentication to get back in. - What do I do if I forget my master password?
When you set up most password managers, they give you recovery codes. Store these in a safe place that isn’t connected to the internet, like a safe-deposit box. You might not be able to get back into your vault if you don’t have them. - How can I teach my family members who aren’t very good with technology how to keep their passwords safe?
Use real things like keys and locks to show how phishing works, and make family vaults that are easy to use. Talk about news stories about data breaches a lot so that everyone knows how bad things are.
References
- National Institute of Standards and Technology (NIST). Digital Identity Guidelines: Authentication and Lifecycle Management (SP 800-63B).
https://pages.nist.gov/800-63-3/sp800-63b.html - Open Web Application Security Project (OWASP). Authentication Cheat Sheet.
https://cheatsheetseries.owasp.org/cheatsheets/Authentication_Cheat_Sheet.html - Troy Hunt. “Pwned Passwords.” Have I Been Pwned.
https://haveibeenpwned.com/Passwords - Bitwarden. Master Your Password Security.
https://bitwarden.com - Verizon. 2024 Data Breach Investigations Report.
https://www.verizon.com/business/resources/reports/dbir/ - Yubico. FIDO2 and WebAuthn: An Introduction.
https://www.yubico.com/fido2/ - Google. Build a more secure login with Passkeys.
https://developers.google.com/identity/passkeys - US-CERT. “Avoiding Social Engineering and Phishing Attacks.”
https://us-cert.cisa.gov/ncas/tips/ST04-014